Changelog
Inspect IP addresses directly from the dashboard
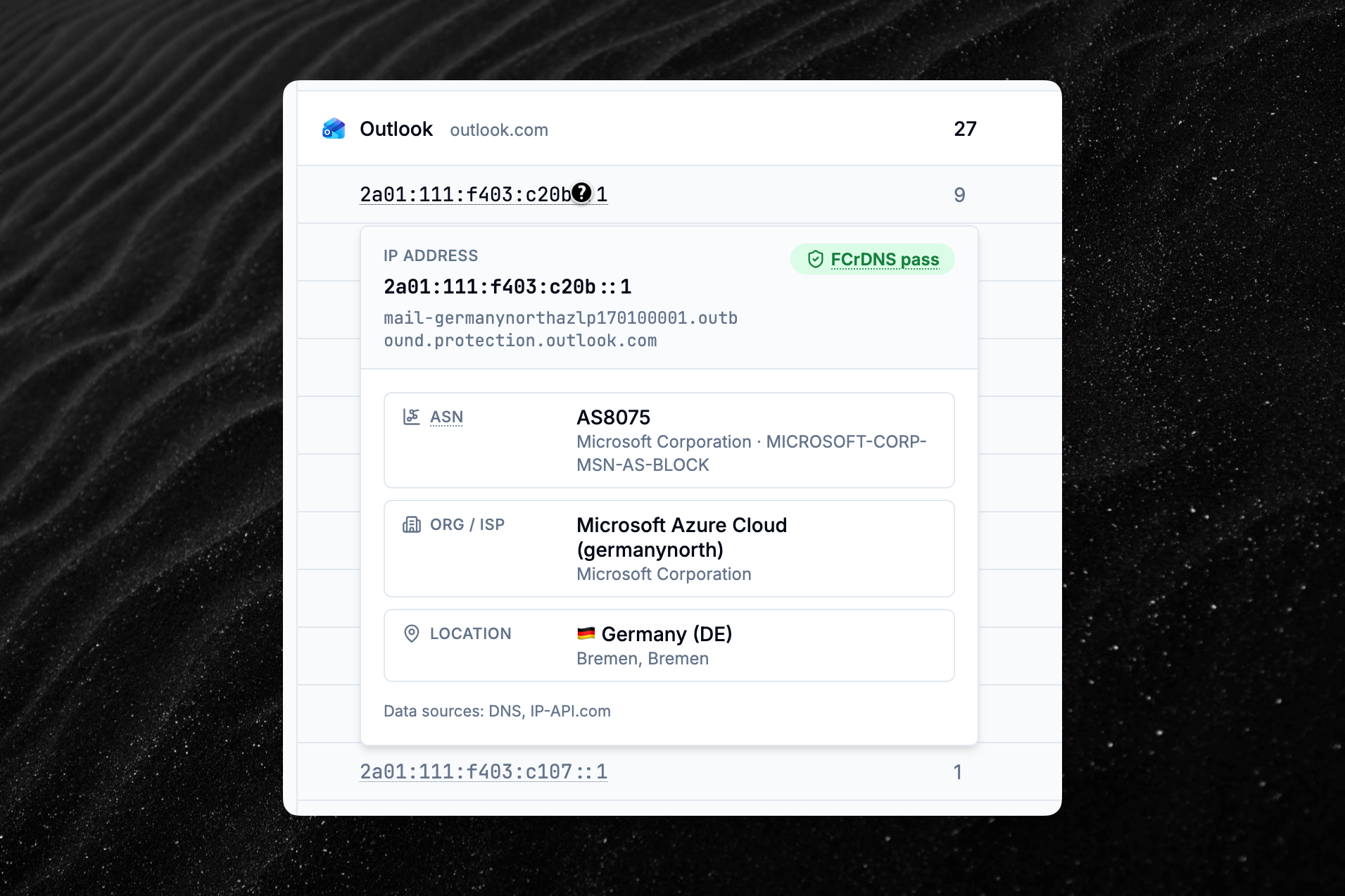
You can now hover over any IP address in the dashboard to quickly inspect it without leaving the page.
The new IP inspection card shows:
- Reverse hostname (rDNS) and FCrDNS status (verifies that the hostname resolves back to the same IP).
- ASN: the Autonomous System Number and its name.
- Organization / ISP: the organization or ISP that owns the IP.
- Location: country, region and city.
The IP inspection card is available throughout the dashboard, including the Sources page, individual DMARC and TLS reports, and diagnosis results.
API access is now available to all customers
We’re excited to launch the initial version of the DMARCwise API, which allows customers to integrate DMARCwise into their workflows and automate DMARC management.
The API is already available to all customers (except for the free plan). This initial version lets you:
- Create/delete domains.
- Create/update/delete domain groups.
- Retrieve the DMARC/TLSRPT setup instructions to automate the setup of DNS records.
- Enable/disable hosted DMARC and manage the hosted DMARC configuration.
- Manually trigger the DMARC/TLSRPT DNS configuration validation.
- Retrieve some basic domain stats, domain checks and validation issues.
To learn how to access the API and how authentication, permissions, rate limits, etc. work, please refer to the API documentation.
If you have any feedback or would like to request additional features/endpoints for the API, please get in touch.
Improved weekly digests deliverability
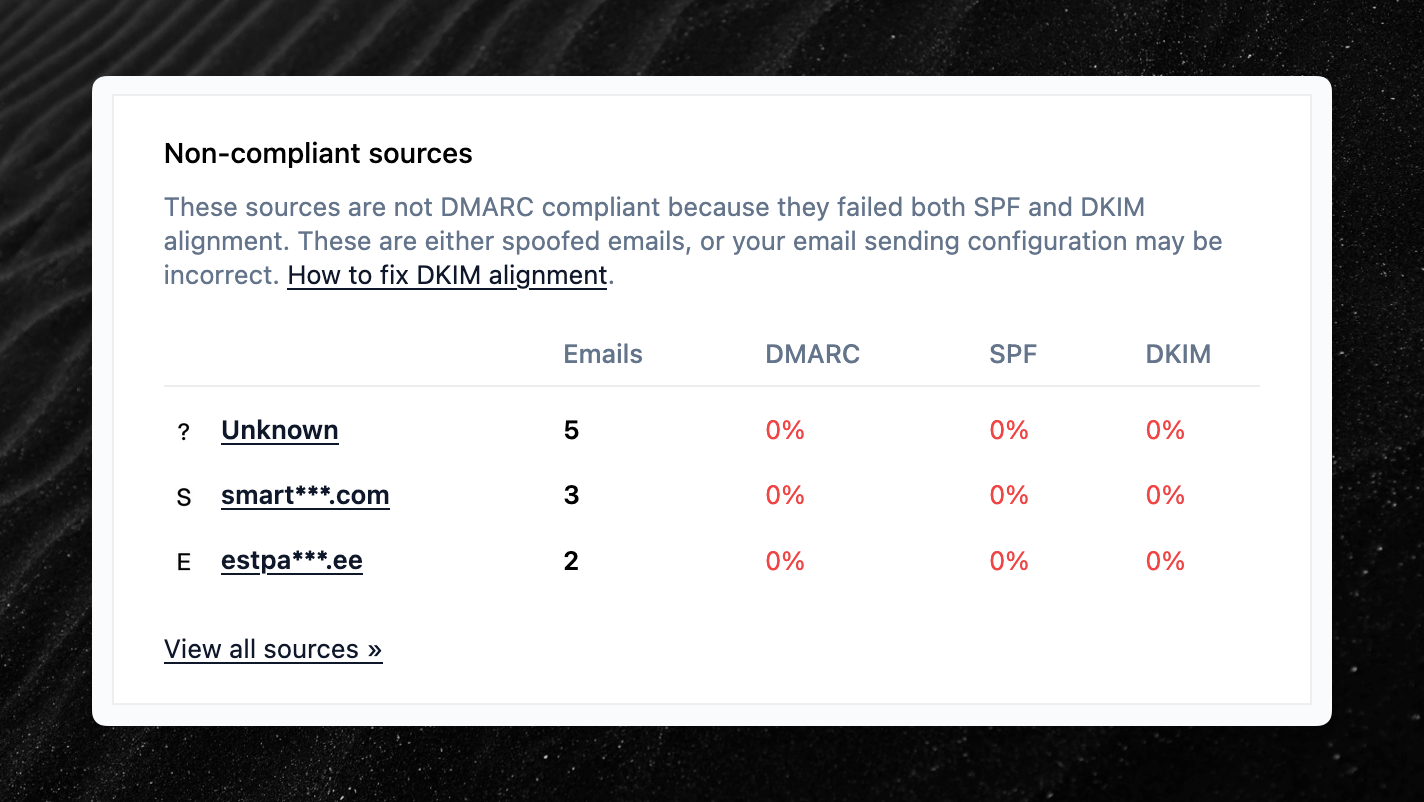
We’ve made some small changes to the formatting of our weekly email digests, with the goal of improving deliverability.
The most noticeable change is that we now obfuscate low-reputation hostnames to prevent email security filters from flagging or blocking the emails.
You may therefore sometimes see redacted hostnames, like in the following example. You can always click on a specific source to view the full details.
Organization owners can now transfer ownership to other users
It is now possible for organization owners to transfer ownership to another user in the organization without contacting support.
To transfer ownership, head over to the Settings page, choose Members, and click on the menu next to the user you want to transfer ownership to. The transfer takes effect immediately and the new owner will have full control over the organization, including the permission to delete the organization or accept the Data Processing Agreement (DPA).
Improved weekly DMARC digests email subject
We’ve improved the weekly DMARC digests so that the email subject line is more informative: the new colored emoji at the beginning of the subject line indicates whether the DMARC compliance level is good or needs attention.
Here are some examples and their meaning:
| Subject | Meaning |
|---|---|
| 🟢 [example.com] DMARC digest for 2 Feb 2026 - 8 Feb 2026 | DMARC compliance for the domain is greater than or equal to 90%. |
| 🟡 [example.com] DMARC digest for 2 Feb 2026 - 8 Feb 2026 | DMARC compliance for the domain is between 10% and 90%. |
| 🔴 [example.com] DMARC digest for 2 Feb 2026 - 8 Feb 2026 | DMARC compliance for the domain is less than or equal to 10%. |
| 🟡 DMARC digest for 2 Feb 2026 - 8 Feb 2026 | Combined digest with the worst DMARC compliance level for a domain being less than or equal to 10%. |
| 🟡 [Group name] DMARC digest for 2 Feb 2026 - 8 Feb 2026 | Combined digest for a domain group with the worst DMARC compliance level for a domain being less than or equal to 10%. |
Updates to our privacy policies, Data Processing Agreement and Terms of Service
Effective 21 January 2026, we updated our privacy documentation and Terms of Service, and published a Data Processing Agreement (DPA) to support GDPR requirements.
The core DMARCwise service and how it processes data have not changed; this update reflects a full review of our documentation and internal procedures.
The affected users have been notified today.
Review the new documentation in the Privacy and GDPR and Terms of Service pages.
Two-factor authentication (2FA) is now available for all users
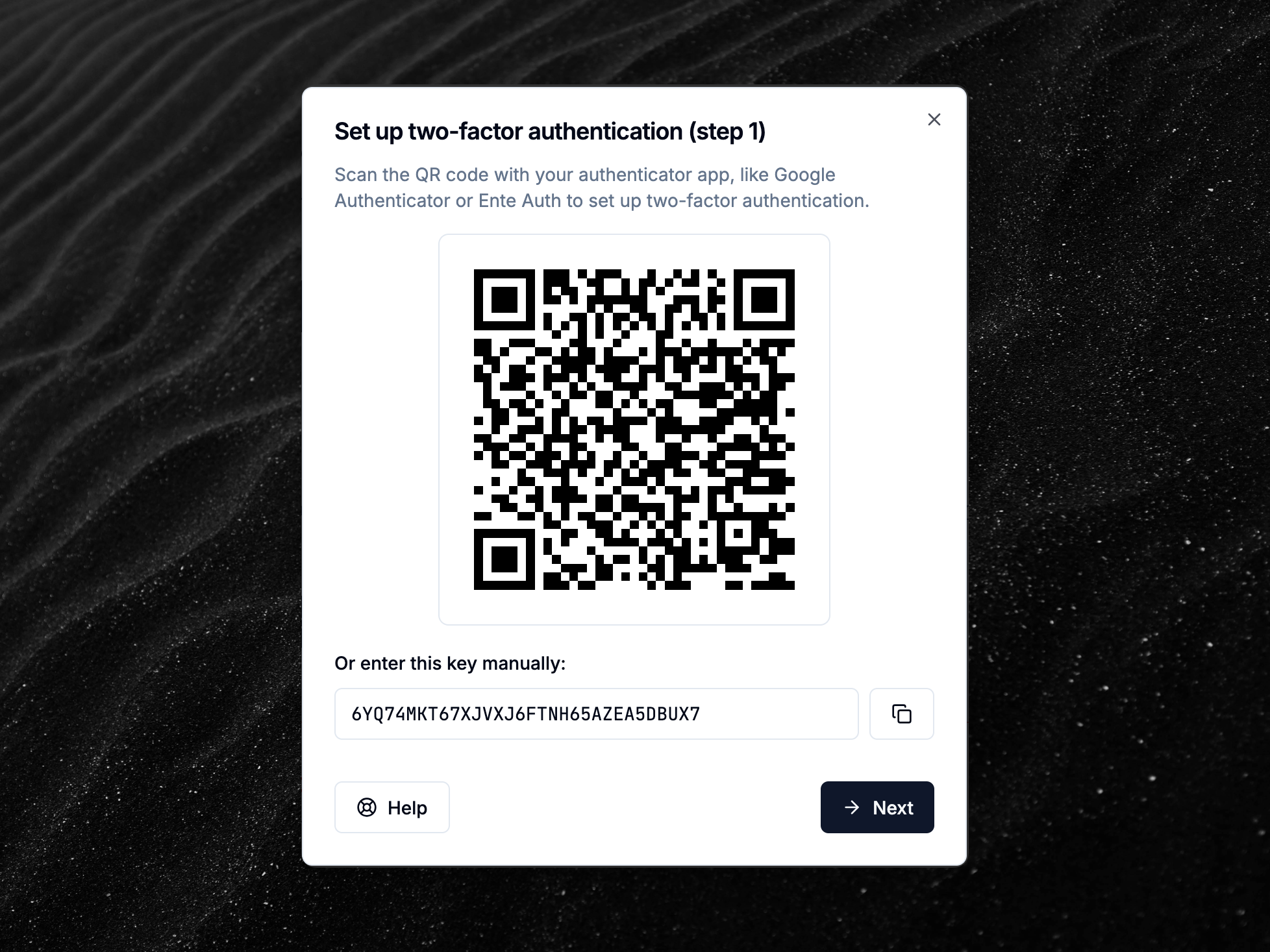
Two-factor authentication (2FA) is now available for all users, adding an extra layer of security to your account.
The 2FA implementation is based on the Time-based One-Time Password (TOTP) algorithm. When enabled, you’ll be prompted to enter a 6-digit code from your authenticator app every time you log in to your account.
Note that if your organization uses Single Sign-On (SSO), 2FA is managed by your identity provider (e.g., Microsoft Entra ID, Okta, Google Workspace) and not within DMARCwise.
Read more about 2FA support in our documentation.
Customers can now delete organizations and users from the dashboard
It is now possible to delete organizations without contacting support. To do so, head over to the Settings page, choose Danger zone and then click on Delete organization. All domains, users, and data will be permanently deleted.
As part of this change, removing a user from an organization now deletes the user from the system permanently. Previously, the user membership would be removed but the user account would continue to exist.
This change is possible now that we discontinued multi-organization access (see previous changelog entry) and makes it easier for companies to manage the data of their employees.
This change also applies to MSP customers and the clients feature: removing a user from a client or deleting the client now deletes the user from the system.
Users can no longer belong to multiple organizations
Starting 5 January 2026, users can only belong to a single organization. Previously, users could join an unlimited number of organizations and switch between them from the user menu in the top right corner of the dashboard.
We’ve made this change to simplify the backend implementation, GDPR compliance and the design of future features planned for this year.
Existing memberships:
The multi-organization feature was used by very few users (less than 1%) and most of the affected organizations are inactive or with expired trials. We’ll soon contact a portion of these users where more than one organization is active and we can’t resolve the conflict unilaterally.
Team members:
While working on this change, we’ve also reworked how team members work: users are now created immediately when you add them, and they can set up their password by following the link received via email.
Previously, users would receive an invitation link to create an account and then join the organization. The new system makes it clearer that when you add a user it automatically belongs to the organization (and only to that organization).
We’ll soon add more controls on user deletion to provide an additional data erasure tool to companies in accordance with our GDPR data processor role.
Read more about how team members work in the documentation.
New “Owner” role:
There is also a new Owner role which is automatically assigned to the creator of the organization. The organization owner will be the only user allowed to delete the organization once we implement this feature.
We’ll also be adding a way to transfer ownership between users.
Read more about roles in the documentation.
If you have questions on how these new changes may affect your setup, please contact support.
Introducing DKIM monitoring
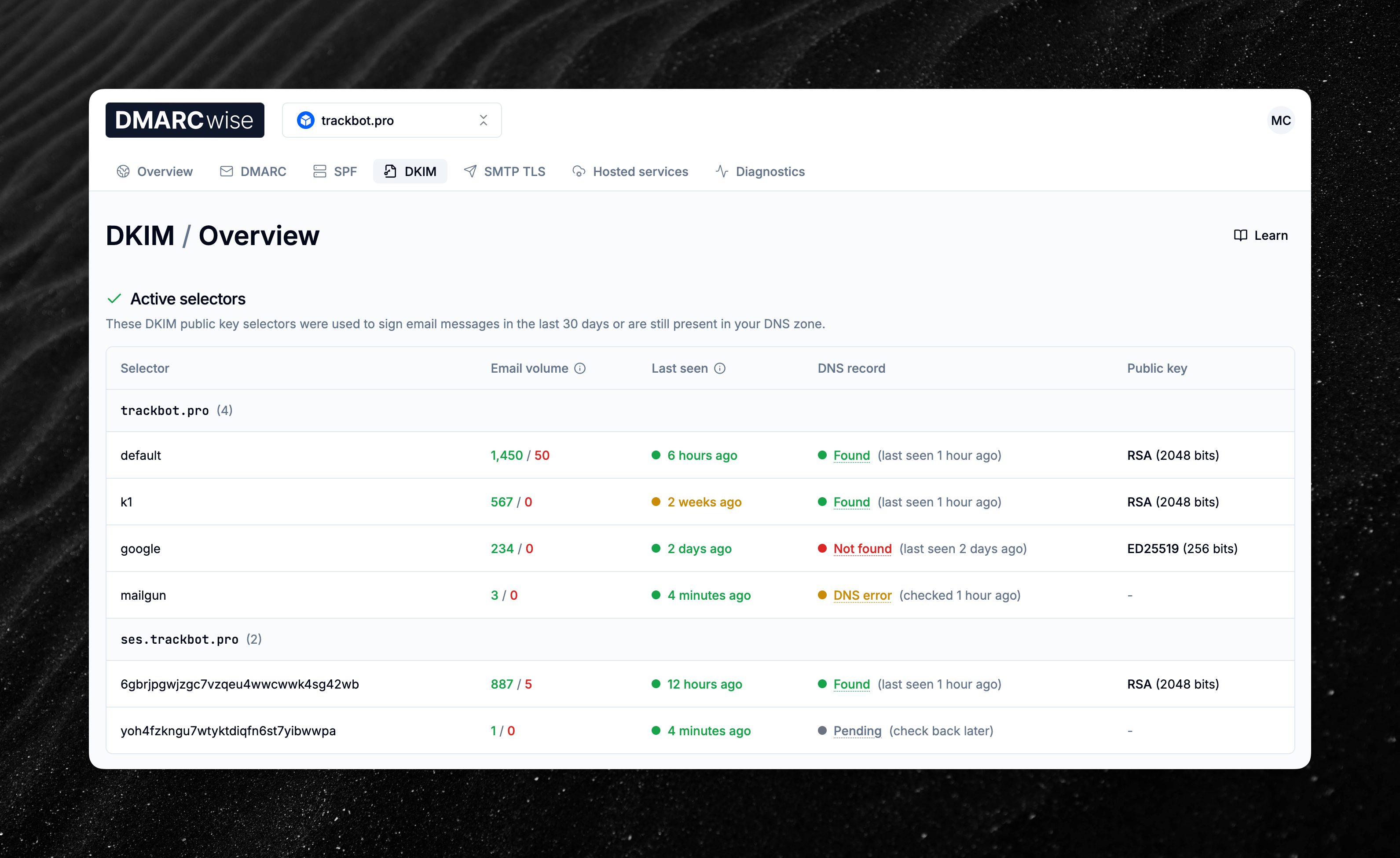
Today, we’re launching a new feature called DKIM monitoring, which adds observability capabilities to the dashboard to monitor DKIM records.
DKIM (DomainKeys Identified Mail) is a cryptographic method for email authentication, playing an essential role in electronic mail.
It is one of the cornerstones on which DMARC is based and it’s therefore important to keep it monitored, ensuring that your domain’s DNS configuration properly includes the DKIM verification records.
Until now, it was hard to obtain this kind of visibility.
The new DMARCwise DKIM monitoring feature solves this: it helps you monitor DKIM by continuously scanning and analyzing your domain’s DKIM records. It does so by extracting the DKIM selectors from the DMARC reports of your domain and then fetching the corresponding DNS records.
For example, if your domain is example.com and you use a selector named selector1, DMARCwise helps you keep track of the fact that you’re using this selector and that the DNS record at selector1._domainkey.example.com must be present and valid until you use the selector.
A DNS record is missing? Some records are unused?DMARCwise lets you easily spot these issues.
To try out the new DKIM monitoring feature, head over to the dashboard, choose a domain and switch to the new DKIM tab.
You’ll see two tables:
- Active selectors shows DKIM selectors that were seen in DMARC reports in the last 30 days or are still present in the DNS zone configuration of the domain.
- Inactive selectors shows the rest of the DKIM selectors, i.e. those that haven’t been seen in DMARC reports recently (and therefore likely not used to sign email messages recently) and are not longer present in the DNS zone.
Selectors in each table are grouped by domain name, making it easy to find selectors associated with a specific subdomain.
Note that the DKIM monitoring feature is being introduced in December 2025, so the system won’t be able to tell you if a DNS record existed before that date.
To learn more about the new DKIM monitoring feature and how to interpret the data, visit our dedicated documentation page.
DMARCbis tags in DMARC records are now supported
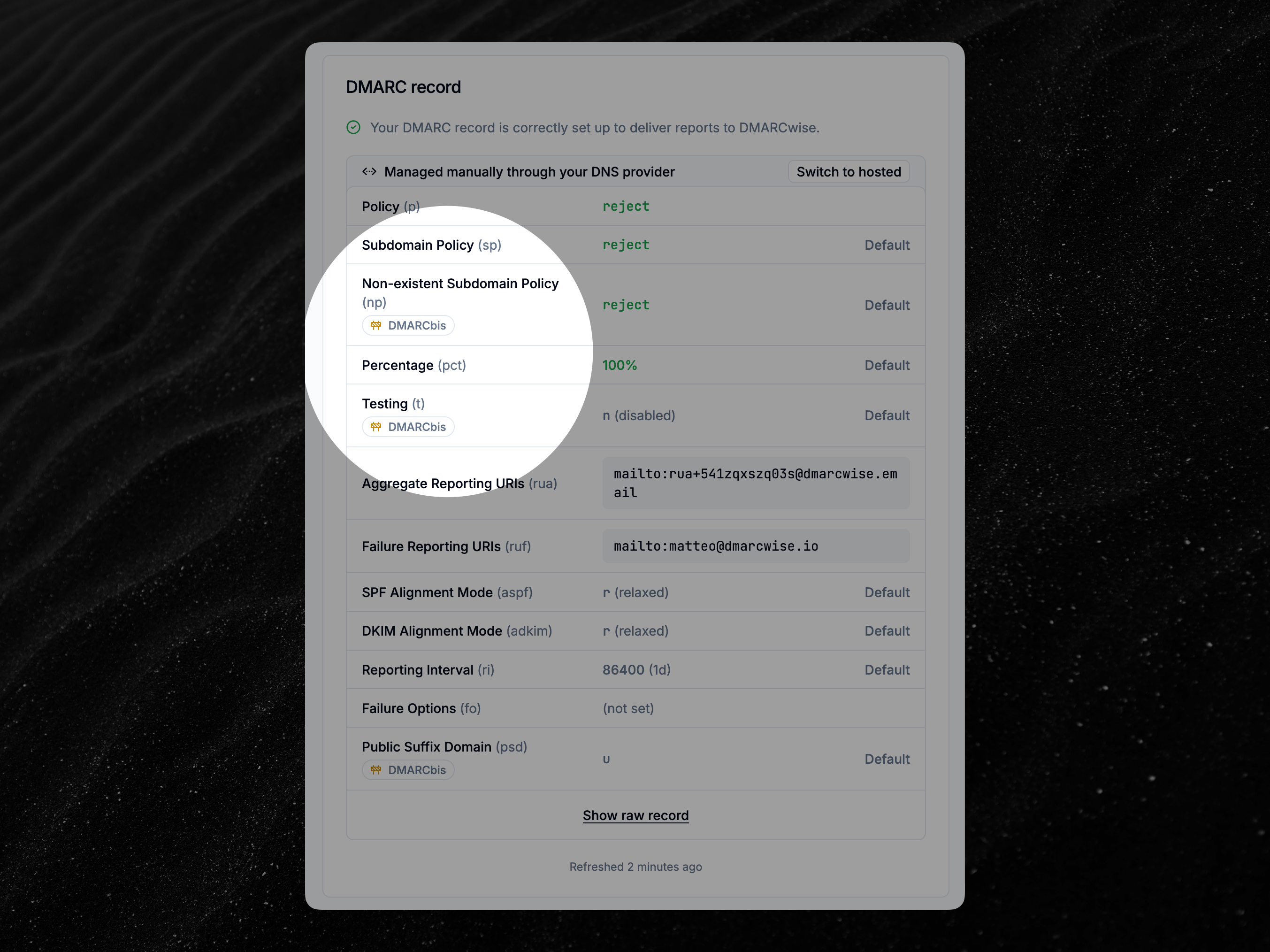
Starting today, DMARCwise fully supports parsing DMARC records that contain tags introduced in the new DMARCbis specification.
DMARCbis is an updated DMARC specification that is expected to be published as a Proposed Standard in the next few months. DMARCwise is now gradually adding support for DMARCbis, since the new specification is in the final stages before publishing.
The following tags are now extracted, validated and shown in the dashboard for each DMARC record:
- Non-existent subdomain policy (
np). - Testing mode (
testing), which replacespctin DMARCbis. - Public suffix domain (
psd).
This applies to all DMARC records, even those that were discovered before today.
Note that most receivers don’t support DMARCbis yet, so these new tags may not have any effect for now.
You can read more about the status of DMARCbis support in this documentation page. Find more information about what’s changing with the new specification in our dedicated article.
DMARCbis reports are now supported
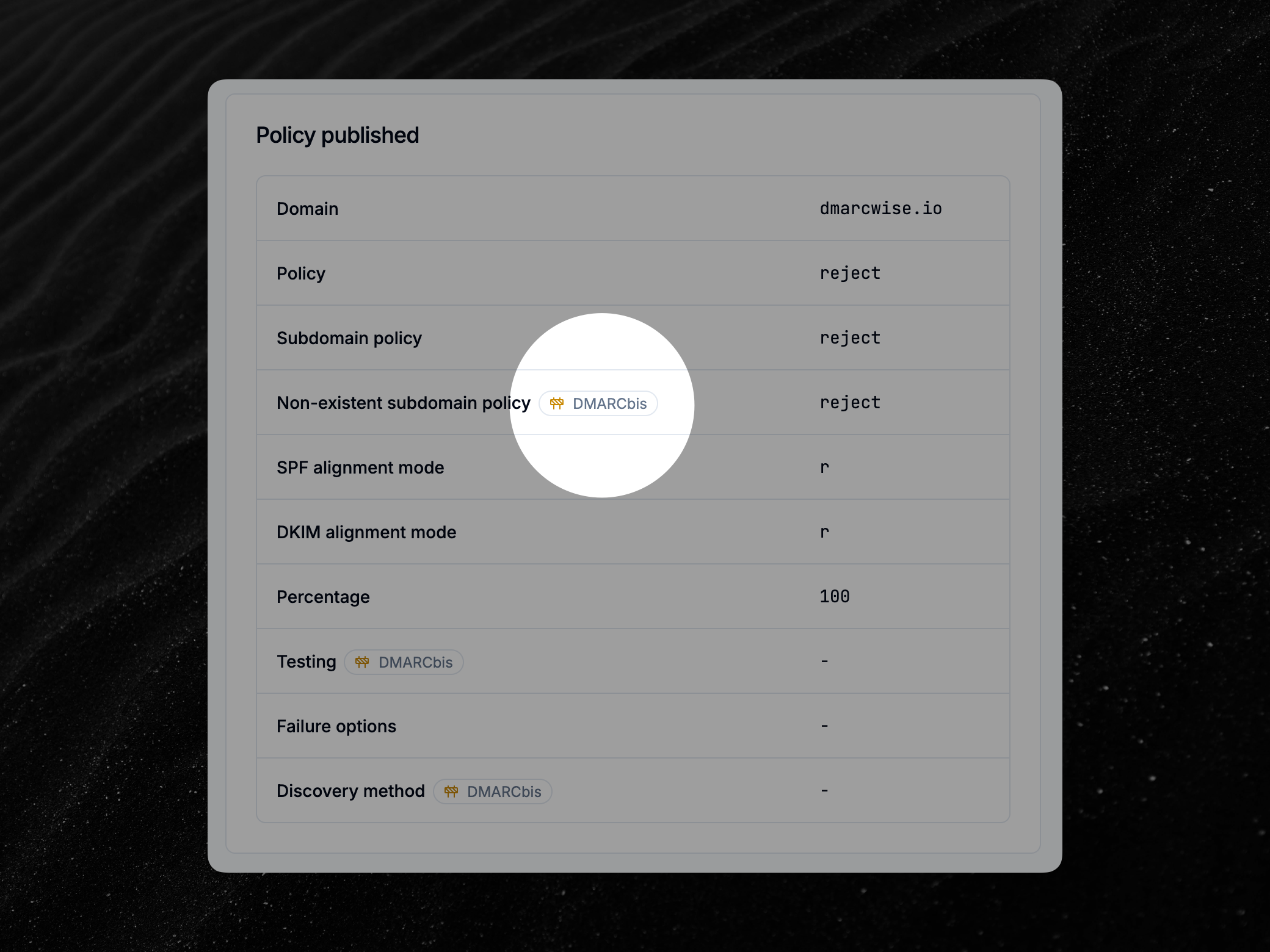
Starting today, DMARCwise fully supports parsing DMARC reports that contain fields introduced in the new DMARCbis specification.
DMARCbis is an updated DMARC specification that is expected to be published as a Proposed Standard in the next few months. DMARCwise is now gradually adding support for DMARCbis, since the new specification is in the final stages before publishing.
We’re starting with an updated report parser that takes into consideration the new fields, which were previously ignored and not shown in the user interface.
The following information is now shown in the dashboard for each report:
- Report generator (
generatorfield). - Non-existent subdomain policy (
np). - Testing mode (
testing), which replacespctin DMARCbis. - Discovery method (
discovery_method), which determines whether the DMARC record was discovered with the old PSL-based approach (psl) or the new tree walk algorithm (treewalk). - Human result for SPF (
human_result).
Additionally, the “disposition” (i.e. the policy applied by a receiver on a set of messages) now accepts the value of pass, which helps distinguish between no action being taken because of a none policy and no action being taken because of a DMARC pass with an enforcing policy. You can find detailed data about the policies being applied by selecting a DMARC source in the dashboard.
Most report generators don’t support DMARCbis yet, so you will not see this data populated most of the time.
You can read more about the status of DMARCbis support in this documentation page. Find more information about what’s changing with the new specification in our dedicated article.
TLSRPT records are now analyzed for syntax errors
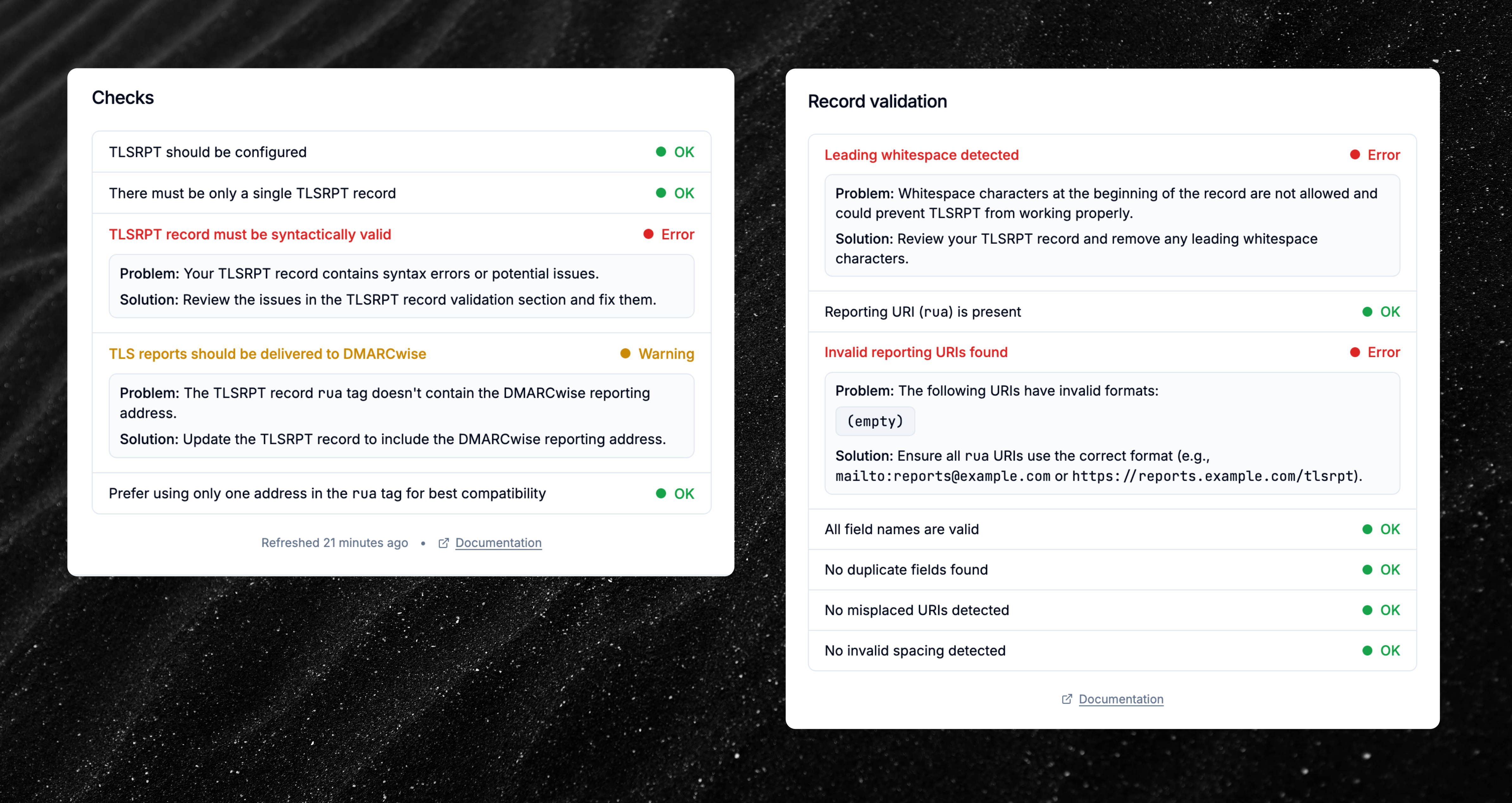
TLSRPT records are now validated by our record parser, which analyzes the syntax to identify issues that could prevent TLS reporting from working properly with mail servers.
Read more in our documentation.
Improved "Add new domain" dialog
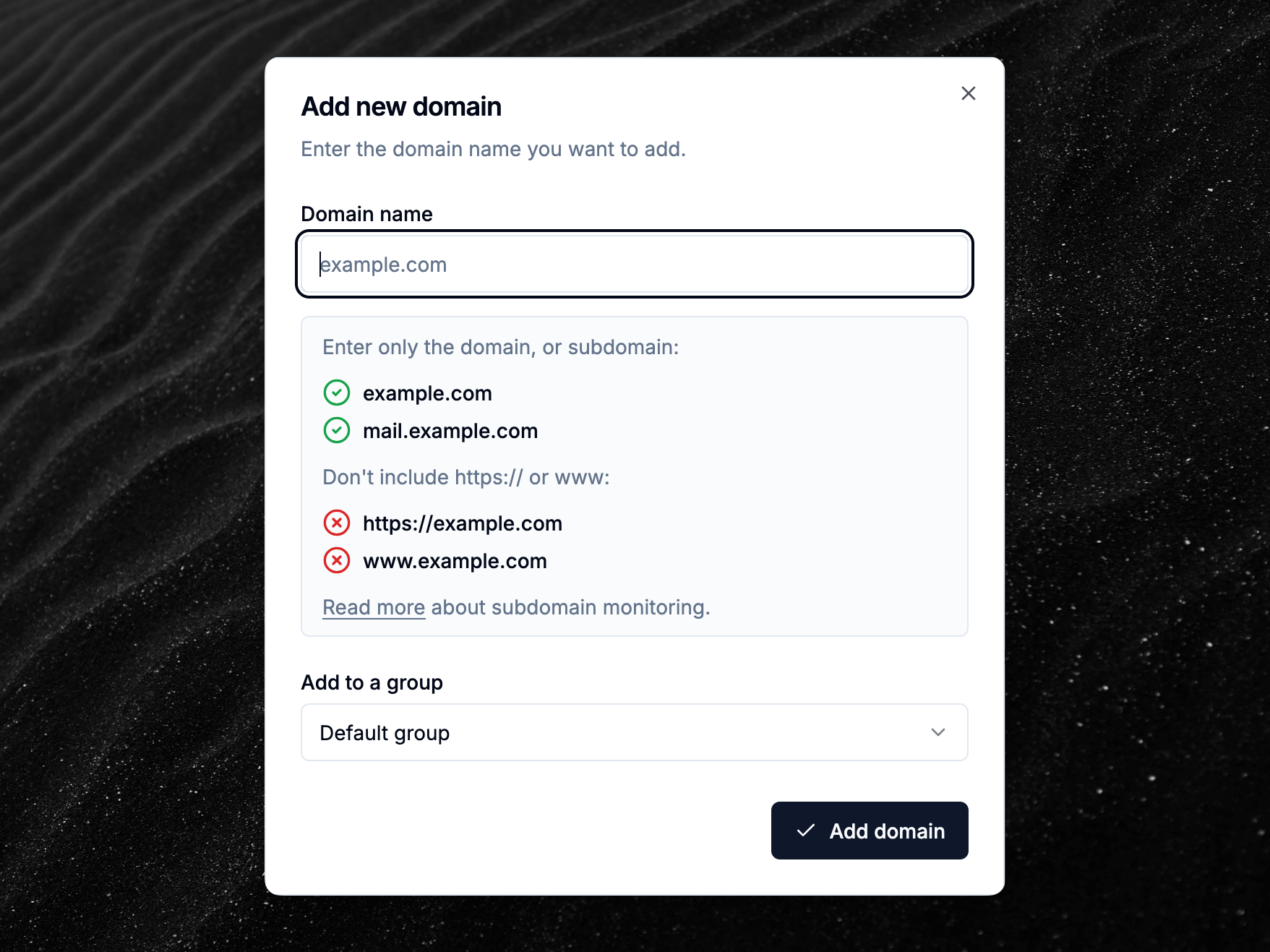
We’ve improved the “Add new domain” dialog, which now shows examples of what is as valid domain name and what is not, for example making it clearer that the www. prefix should not be present.
There is now also a link to the Subdomains documentation page, which explains how DMARCwise and the various protocols work with subdomains, and when you should add them separately in the dashboard.
New domain overview page
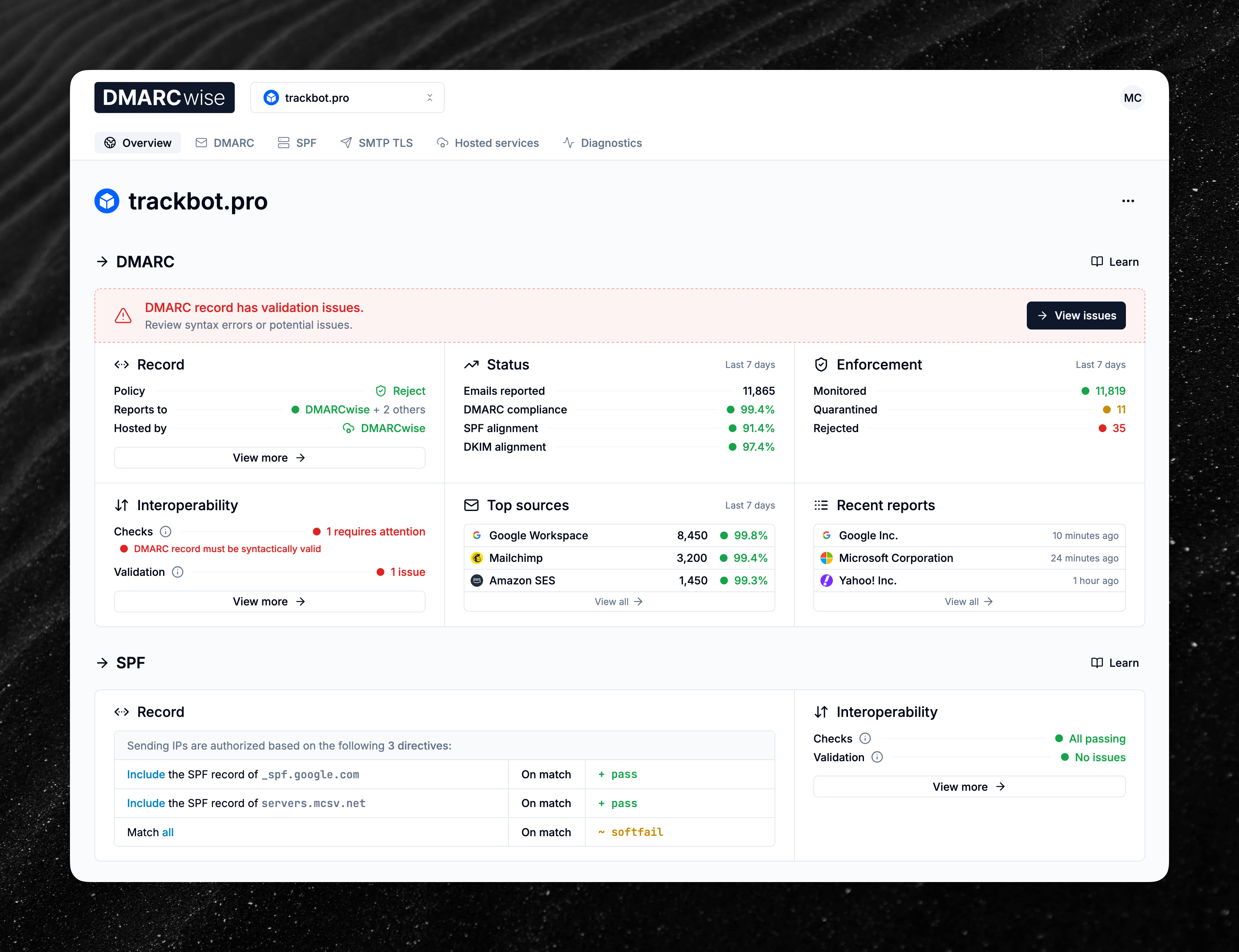
A new domain overview page is now available.
It is now much more detailed than before and aims to be a comprehensive bird eye’s view of your domain, providing the current status, quick statistics, and an easy way to spot issues that require your attention, for DMARC, SPF and SMTP TLS.
Read more in the Domain overview documentation page.
We’ve also moved the Checks feature: find an overview of the failing checks in the domain overview page, and browse the detailed list of checks inside the individual tabs for DMARC, SPF, and SMTP TLS, alongside the record validation results.
Find more about checks and validation for DMARC, SPF, and TLSRPT in the corresponding documentation pages.
Introducing SPF monitoring
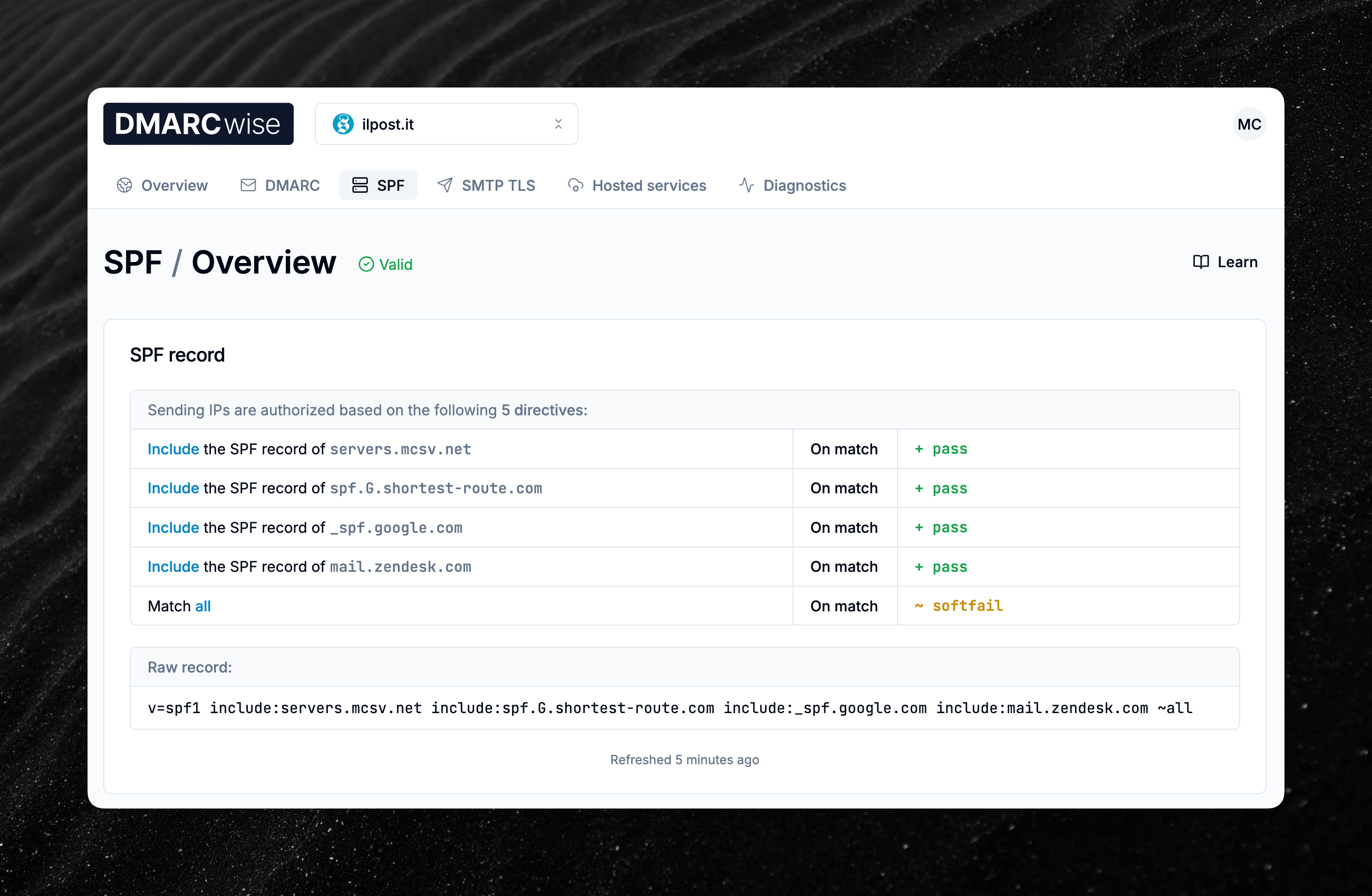
Today, we’re launching a new feature called SPF monitoring, which adds observability capabilities to the dashboard to monitor SPF (Sender Policy Framework) records.
SPF still plays an important role in electronic mail, and is one of the two cornerstones of DMARC.
Until now, it was hard to obtain visibility into SPF records and spot issues and misconfigurations that affect email delivery. The new DMARCwise dashboard solves this:
- In the new SPF tab, the current SPF record will be presented visually and with simple natural language, making it easier to understand what your SPF record does.
- DMARCwise continuously scans and analyzes your domain’s SPF record, producing a list of Checks and Record validation results.
- These two features evaluate the adherence of the configuration to standards and best practices, to ensure best compatibility and interoperability.
- Our SPF analyzer supports all the SPF features and syntax variants and is heavily tested with hundreds of automated tests.
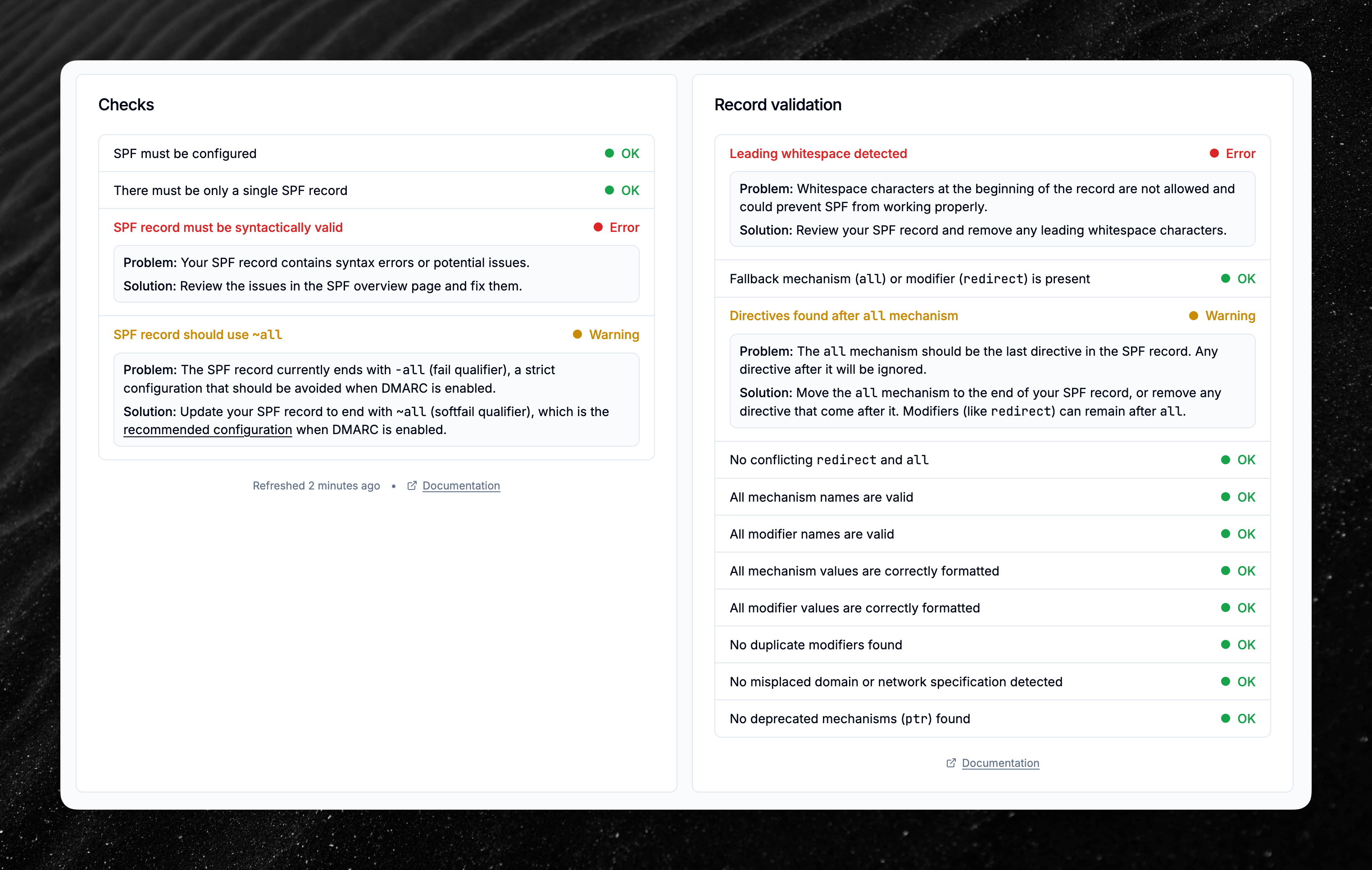
To learn more about the new SPF features, visit our documentation pages:
Stay tuned for further updates around SPF monitoring.
Updated role precedence when using multiple roles with SAML SSO
When passing multiple roles with SAML SSO through the supported roles attributes, we now take the role with the highest level of permissions. Previously, the first one of the list was picked.
Learn more in our SSO documentation.
All paid plans now include unlimited reporting volume
Starting today, all DMARCwise paid plans include unlimited reporting volume.
Previously, subscription plans such as Starter and Growth had a soft limit on the number of DMARC-complaint emails detected per month (as reported through DMARC reports).
The limit is now completely removed, and the price of subscription plans stays the same. Enjoy!
This change doesn’t affect the free plan, but it applies to the non-profit plan.
New trends charts for DMARC and TLSRPT data
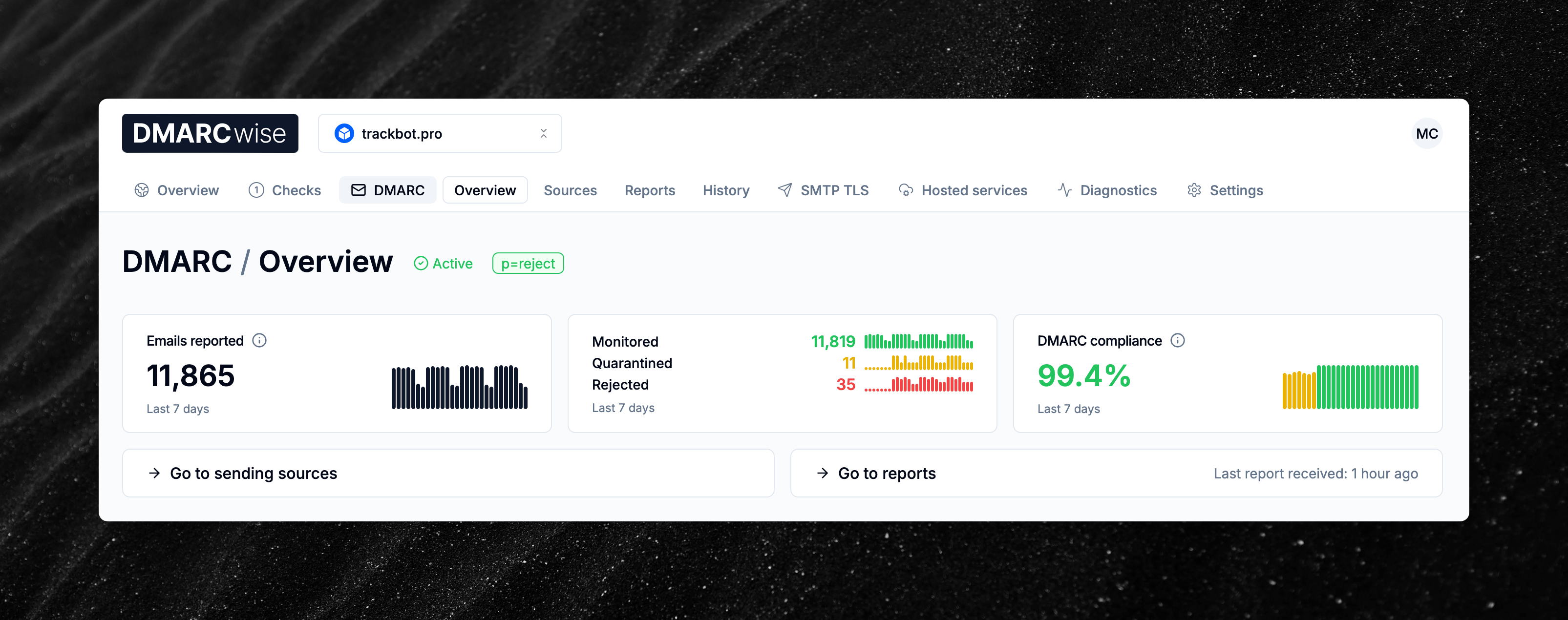
The DMARCwise dashboard now shows useful charts to monitor the trend of key metrics over time.
Specifically, the new charts help you monitor these metrics over time:
- Total emails reported.
- Amount of monitored/quarantined/rejected emails.
- DMARC pass/fail.
- SMTP TLS success/failure sessions.
Hover over a chart to see the corresponding metric value for the past 30 days.
New SSO setup guide for Google Workspace
SAML SSO is now fully compatible with Google Workspace after our testing, and we now provide a dedicated guide to set it up.
Although our SSO implementation theoretically works with any generic SAML implementation, each Identity Provider has their own peculiarities and we want to ensure the most commonly used ones are properly tested by us.
Read the Google Workspace SSO setup guide for more information, including how to set up access control and application roles.
Improved support for SSO roles and access control
We’ve made some improvements to the SAML SSO implementation to allow passing roles through SAML attributes and enforcing the presence of a valid role.
Previously, passing application roles from the Identity Provider to DMARCwise was only possible/documented when using Microsoft Entra ID.
Now it’s possible to use the custom SAML response attribute named urn:dmarwise:role to pass a role. DMARCwise will automatically assign and synchronize the role when the user logs in to DMARCwise with SSO.
In addition to this, it’s now possible to require the presence of a valid role attribute for every login. This is useful when using Identity Providers that don’t have an easy way to restrict who can use applications out of the box (e.g. Keycloak): users without a valid role attribute won’t be able to log in to DMARCwise when the option is enabled.
To learn more about roles and access control, read the updated SSO documentation page.
You can also refer to the updated Keycloak setup guide.
You can now choose the statistics period in the domains dashboard
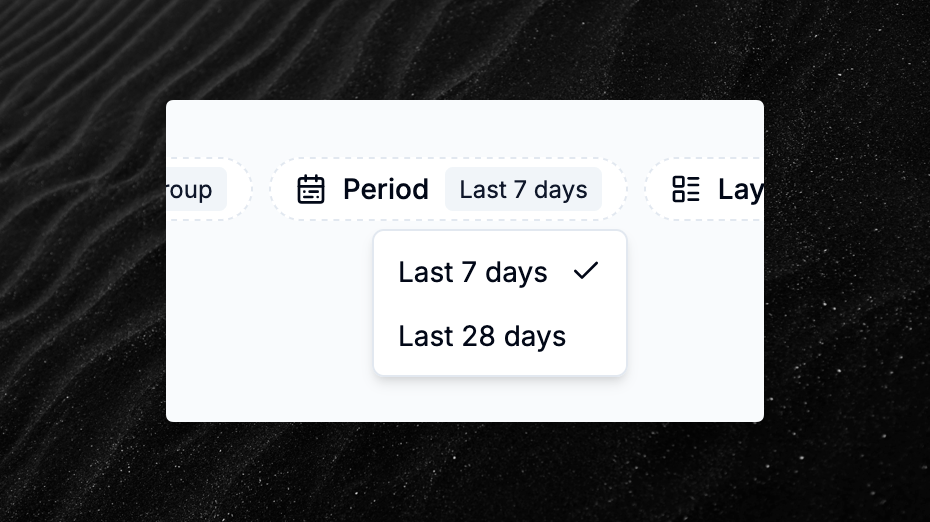
After a request from one of our customers, we’ve added a way to choose the period for which the statistics in the domains list refer to.
You can now choose between:
- Last 7 days (default)
- Last 30 days
Reflecting the period for which statistics such as the total number of reported emails, the DMARC pass percentage, etc. are calculated on.
EU infrastructure migration (part 2) completed 🇪🇺
This weekend, we have completed the second step towards a full migration of the core components of DMARCwise infrastructure to European cloud providers.
The main website dmarcwise.io is now hosted in a European Union country with a fully European cloud provider.
In the coming months we’ll be continuing this process and move other parts of the infrastructure to the EU, where possible. We expect that this will be especially appreciated by our European customers that take great consideration of data location and data privacy topics.
Improved support for Keycloak SSO
For customers using Keycloak as an SSO identity provider, we have just improved our SAML implementation with the aim of simplifying the setup process.
You’ll now find a setup guide specific for Keycloak in the documentation.
Plus, DMARCwise now supports the standard Keycloak attributes for the email address, first name and last name, so you can simply check them in the Keycloak client configuration without the need of manually entering the required claims.
EU infrastructure migration (part 1) completed 🇪🇺
This weekend, we have completed the first step towards a full migration of the core components of DMARCwise infrastructure to European cloud providers.
Our main database with all customer data is now hosted in a European Union country with a fully European cloud provider.
At the same time, we have reworked most of our infrastructure architecture to make it more reliable, resilient, faster and secure than before.
In the coming weeks and months we’ll be continuing this process and move the remaining parts of the infrastructure to the EU, where possible. We expect that this will be especially appreciated by our European customers that take great consideration of data location and data privacy topics.
New option to use semicolon separators in CSV export
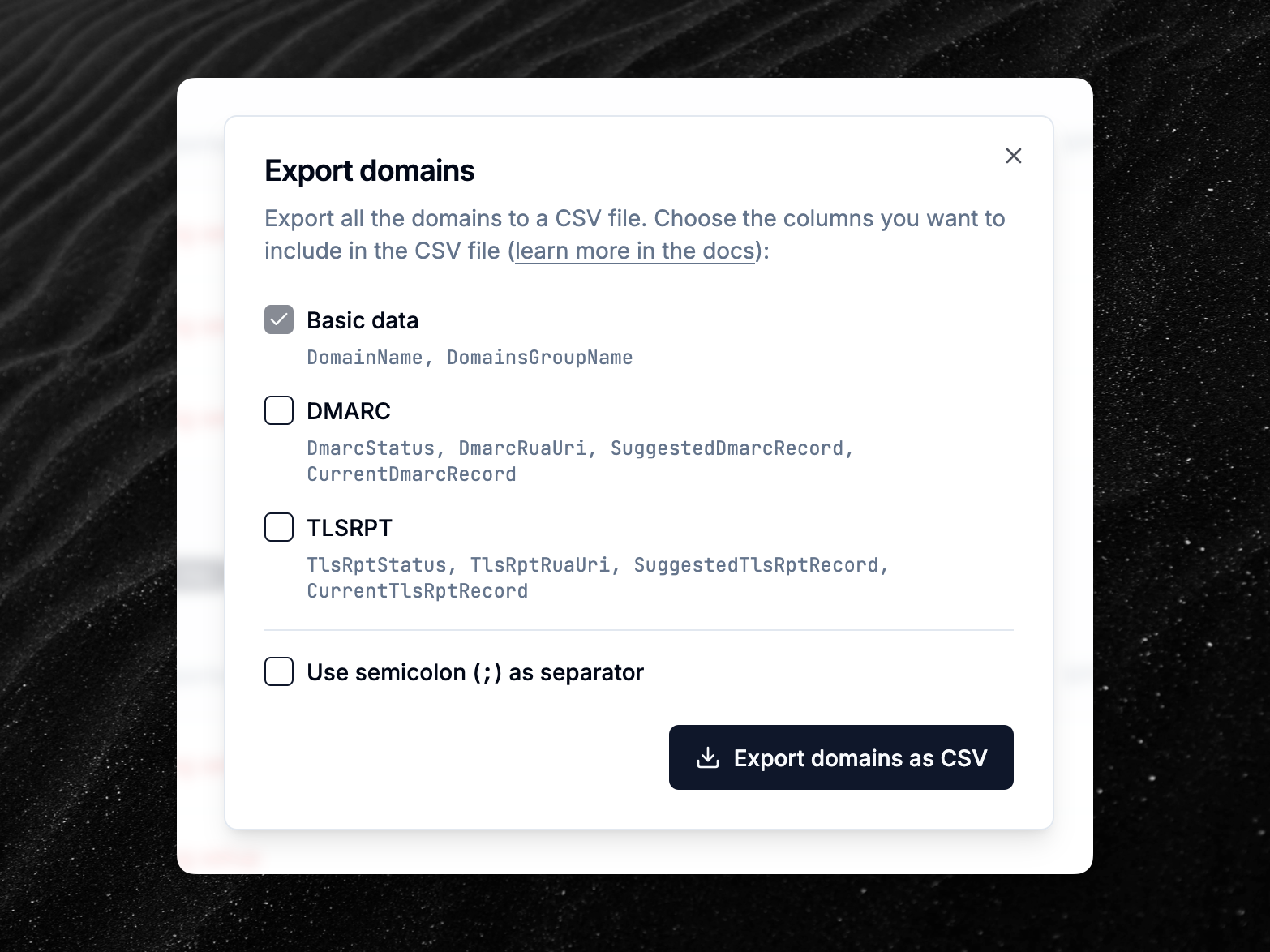
When exporting domains to a CSV file, you can now optionally choose to use semicolons (;) instead of commas (,) as separators.
This can be useful when importing the CSV file in Microsoft Excel, which often expects semicolons by default in some countries.
Learn more in the export documentation.
Customize the domains list with the new Focus feature
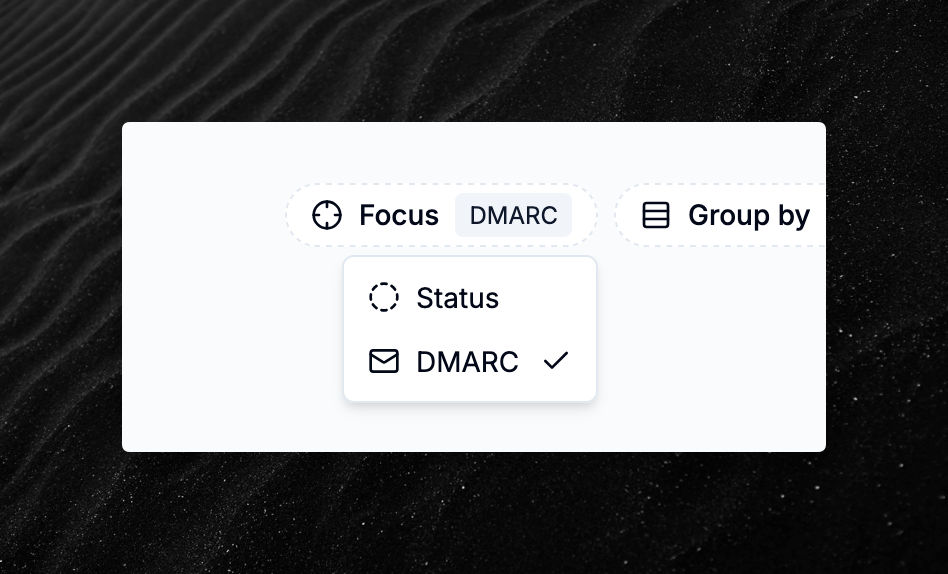
We have added a new view option to configure which data columns are shown in the domain list/grid.
You can now choose to focus on Status and see at a glance the configuration status for both DMARC and TLSRPT for all domains.
The default focus remains DMARC.
The Focus feature will be improved to include more choices in the future. It will also be persisted, so that when you refresh the page or access from another device you don’t lose the state.
New MSP clients management user interface
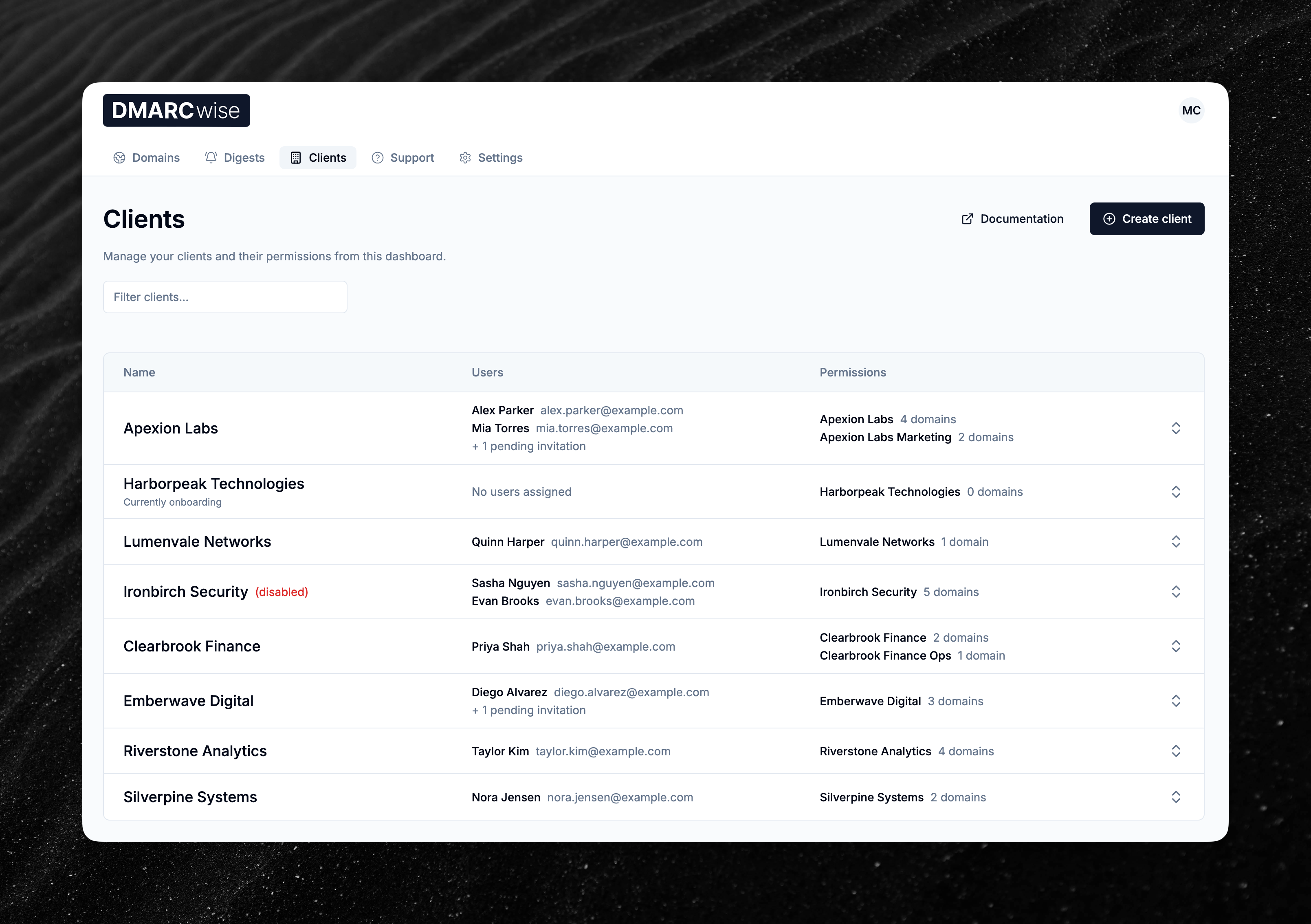
The MSP clients management page has been redesigned to be more compact and provide more information at a glance.
You can still view the details for a client as before by clicking on a row.
The page now also allows for filtering the list of clients by name.
MSPs can now grant write permissions to clients
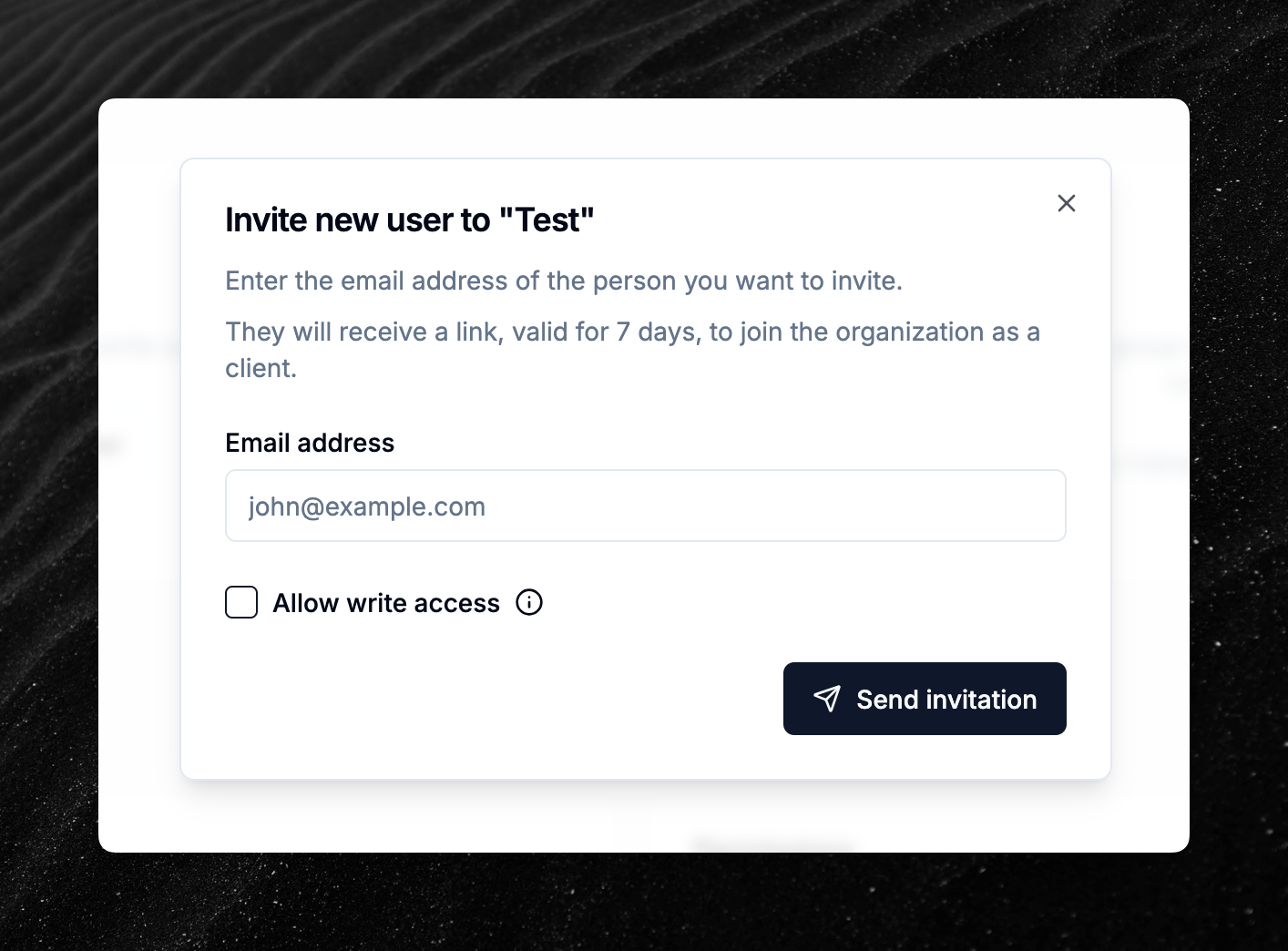
Customers on the MSP plan using the clients feature can now choose whether to grant write permissions to invited users.
When you allow write access, additional permissions will be granted to the user on the domains they have access to. Learn more in the documentation page.
Customers can now change the subscription plan from the dashboard
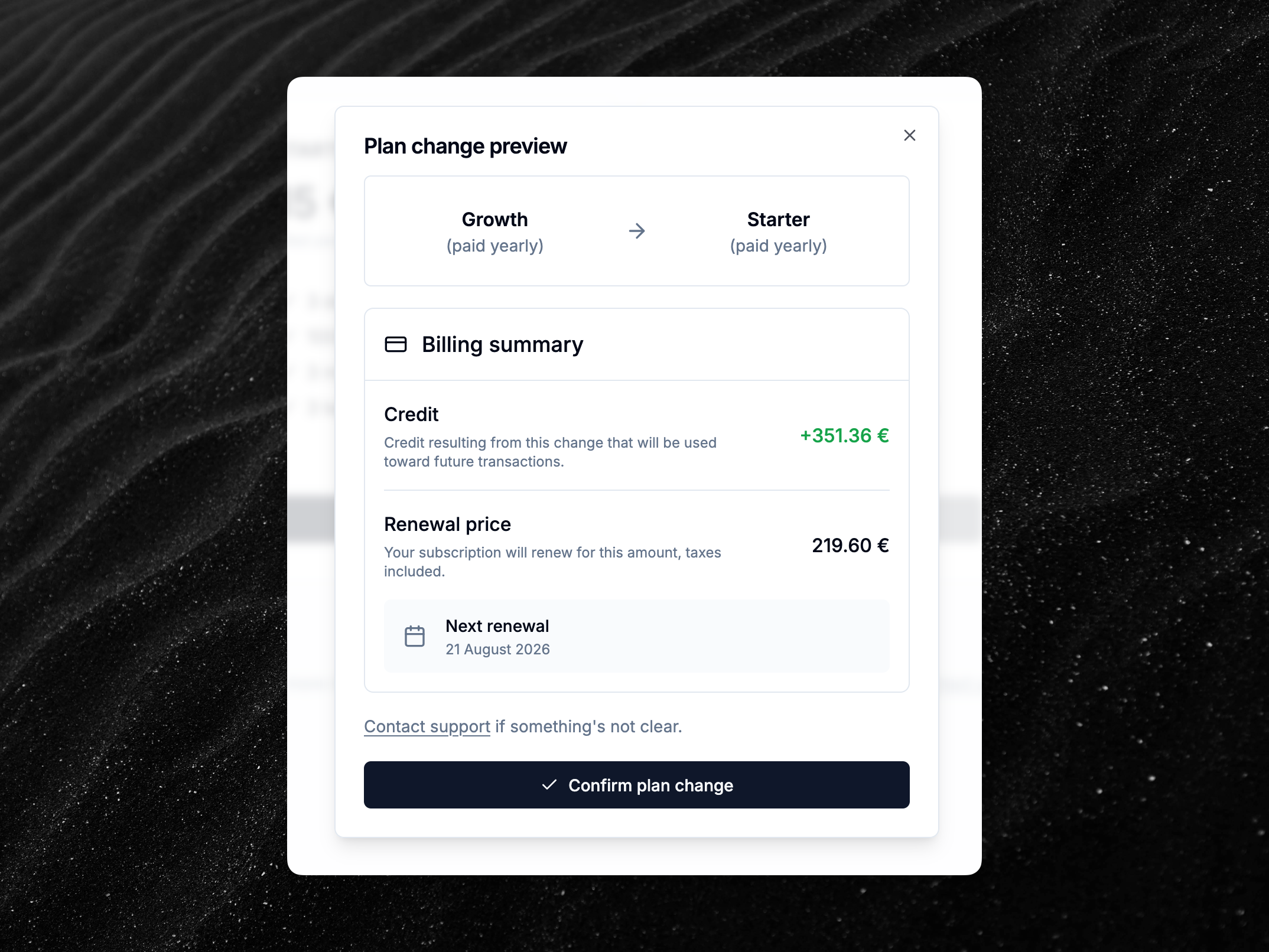
It is now possible to switch between subscription plans without contacting support. Specifically, these changes are now possible from the billing settings:
- Downgrading from the trial plan to the free plan.
- Downgrading from a canceled subscription to the free plan.
- Upgrading/downgrading between paid subscription plans (Starter, Growth, Scale).
- Change the billing interval between monthly and yearly for paid plans (Starter, Growth, Scale).
The plan change preview dialog will alert you if you need to reduce your usage before downgrading to a plan with lower limits or less features.
Customers on the MSP plan or on other custom plans are not affected by this change.
Okta SSO can now be configured from the Okta official Integration Network app catalog
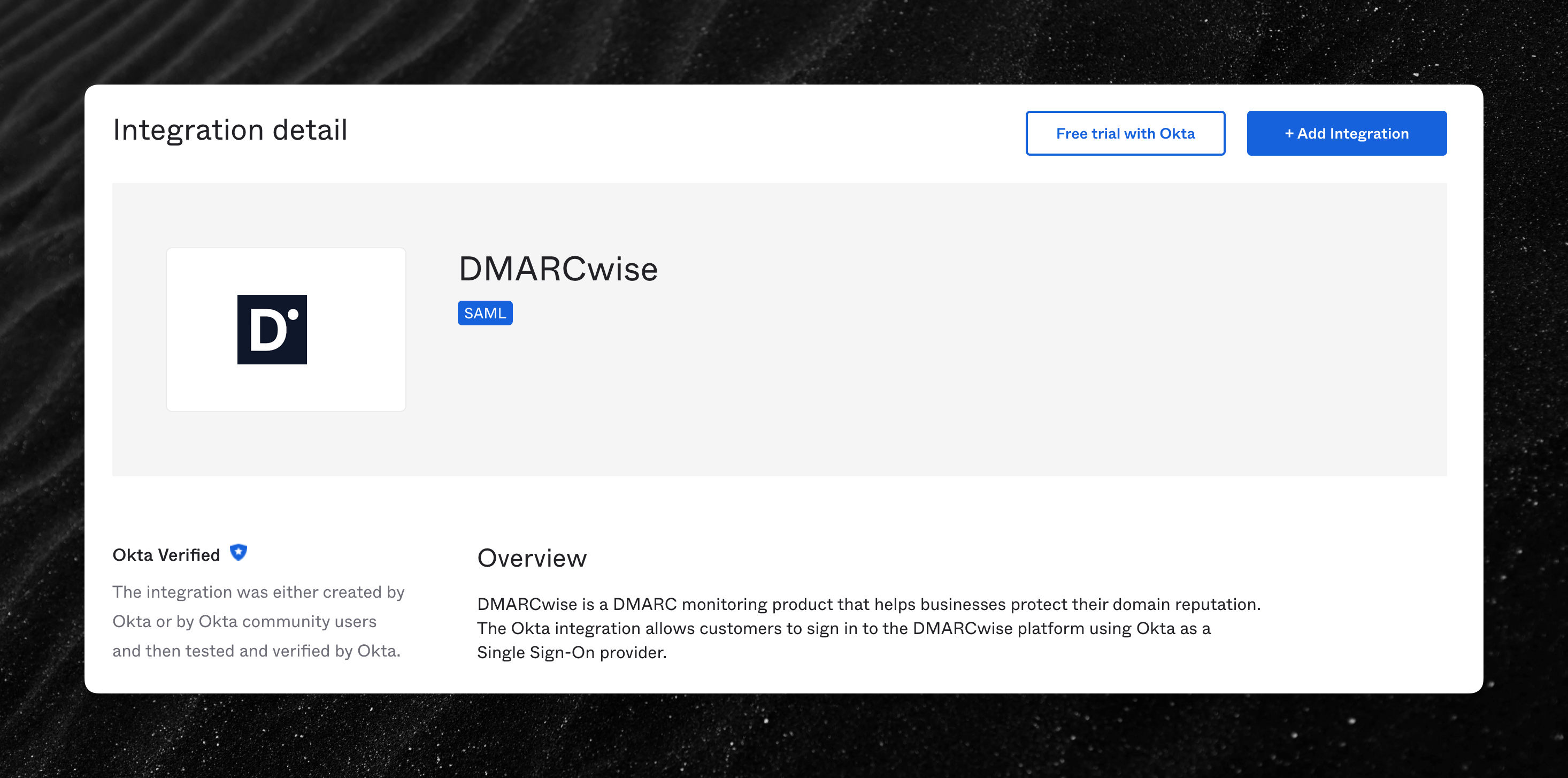
Customers that use Okta as an Identity Provider can now simplify the SSO setup by using the official app published in the Okta Integration Network catalog.
To learn more on how to set up SSO with Okta, consult our documentation.
New claim for user ID in SAML SSO
We now support the custom urn:dmarcwise:userId claim for situations where you can’t configure the NameID claim to contain a persistent identifier like a user ID.
When using SSO with SAML, it’s important to make sure that the NameID claims contains a persistent identifier such as a user ID or employee ID, and not an email address. This is because the email address may change with time and a NameID change would make it impossible to match the user in DMARCwise upon login.
If you’re unable to change the configuration of the NameID claim, you can now create a custom claim with type urn:dmarcwise:userId: if the NameID format is not declared as persistent and urn:dmarcwise:userId is present, the urn:dmarcwise:userId will be used in place of the NameID.
Learn more in the SSO documentation.
Duplicate reports are now discarded
Starting 1 August 2025, duplicate DMARC and TLSRPT reports are automatically detected and discarded.
Some email service providers like Google are in fact known to sometimes deliver several copies of the same report, leading to incorrect statistics.
A report is now detected as duplicate if an identical report was received from the same sender in the previous 24 hours.
Although the DMARC specification suggests the use of the Report-ID for deduplication, some email providers tend to reuse the same IDs over short periods of time, therefore we’ve opted for a stricter algorithm.
Email address update now possible from the dashboard
Users can now change the email address associated with their account from the account settings.
Changing the email address requires following the confirmation link received via email. After confirmation, all the login sessions will be terminated and the old email address will receive an email alert.
Follow this changelog with the RSS feed
We have published an RSS 2.0 feed for the DMARCwise product changelog. You can access it at this URL:
Introducing hosted DMARC
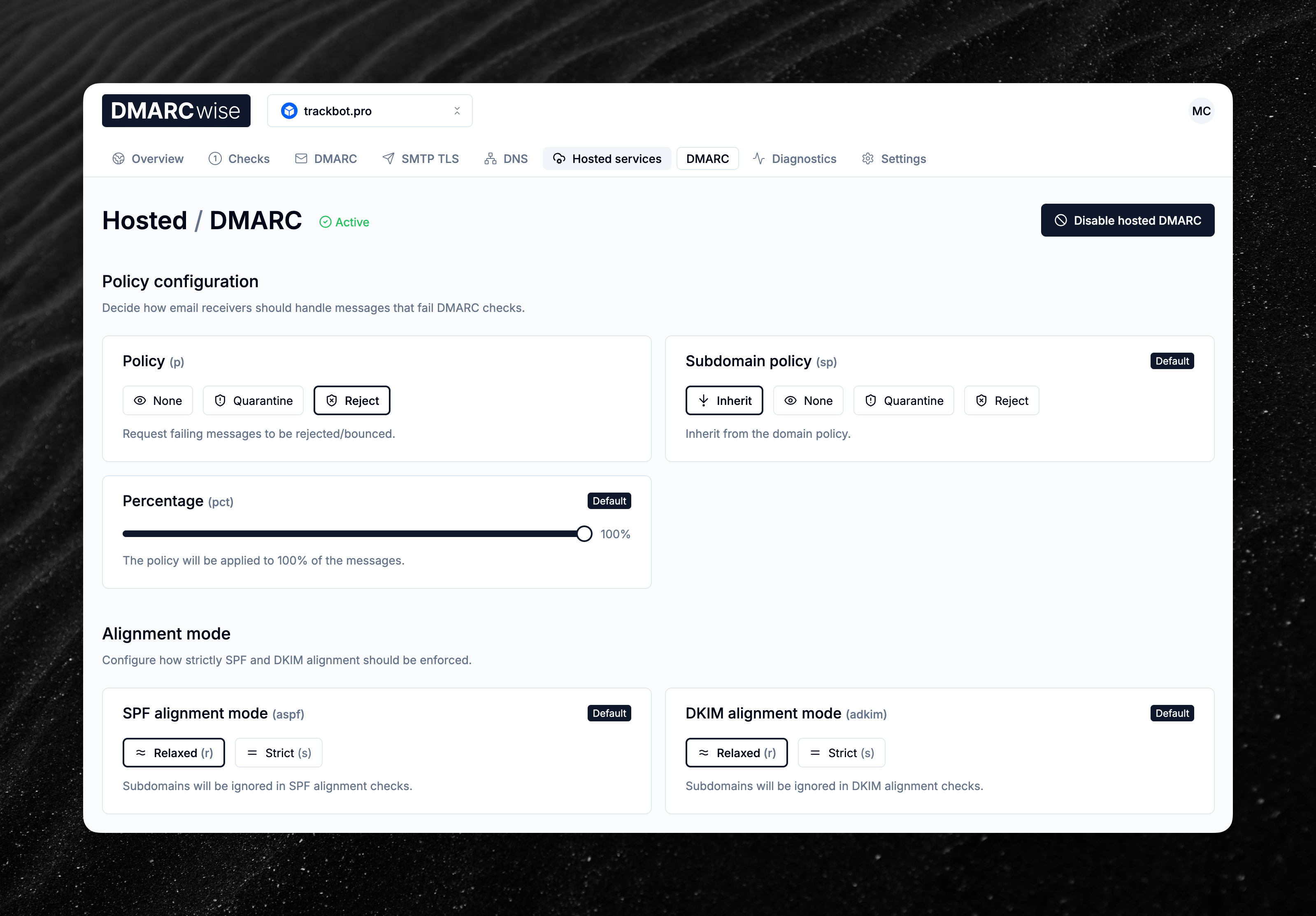
Today, we’re launching a new feature called hosted DMARC.
With hosted DMARC, you can delegate the management of the DMARC DNS record to DMARCwise with a CNAME (alias) record.
You’ll then be able to manage the DMARC configuration from the dashboard, without going through your DNS provider for every change.
You can learn more about hosted DMARC and how to set it up for existing or new domains in our new documentation pages:
Improved validation of DMARC failure options
We have improved the validation of the fo tag in DMARC records. The fo tag stands for failure options and allows a domain owner to decide in which cases a failure report should be generated.
There are strict rules around the formatting and accepted values of the fo tag, and we have noticed that users often get it wrong.
For example, the following tag is valid:
fo=0:d:s
While these ones are not:
fo=0:1
fo=0:0
(0 and 1 are mutually exclusive and there can be no duplicates.)
DMARCwise’s DMARC record validator now catches this issue and shows an error about it in the dashboard.
Existing records were re-scanned and so you may see new issues being reported in the dashboard.
Keep in mind that the fo tag must be used only when the ruf tag is also specified. DMARCwise doesn’t currently support the processing of failure reports, but you can specify an email address of yours in the ruf tag to receive these (rare) reports.
Introducing DMARC record validation
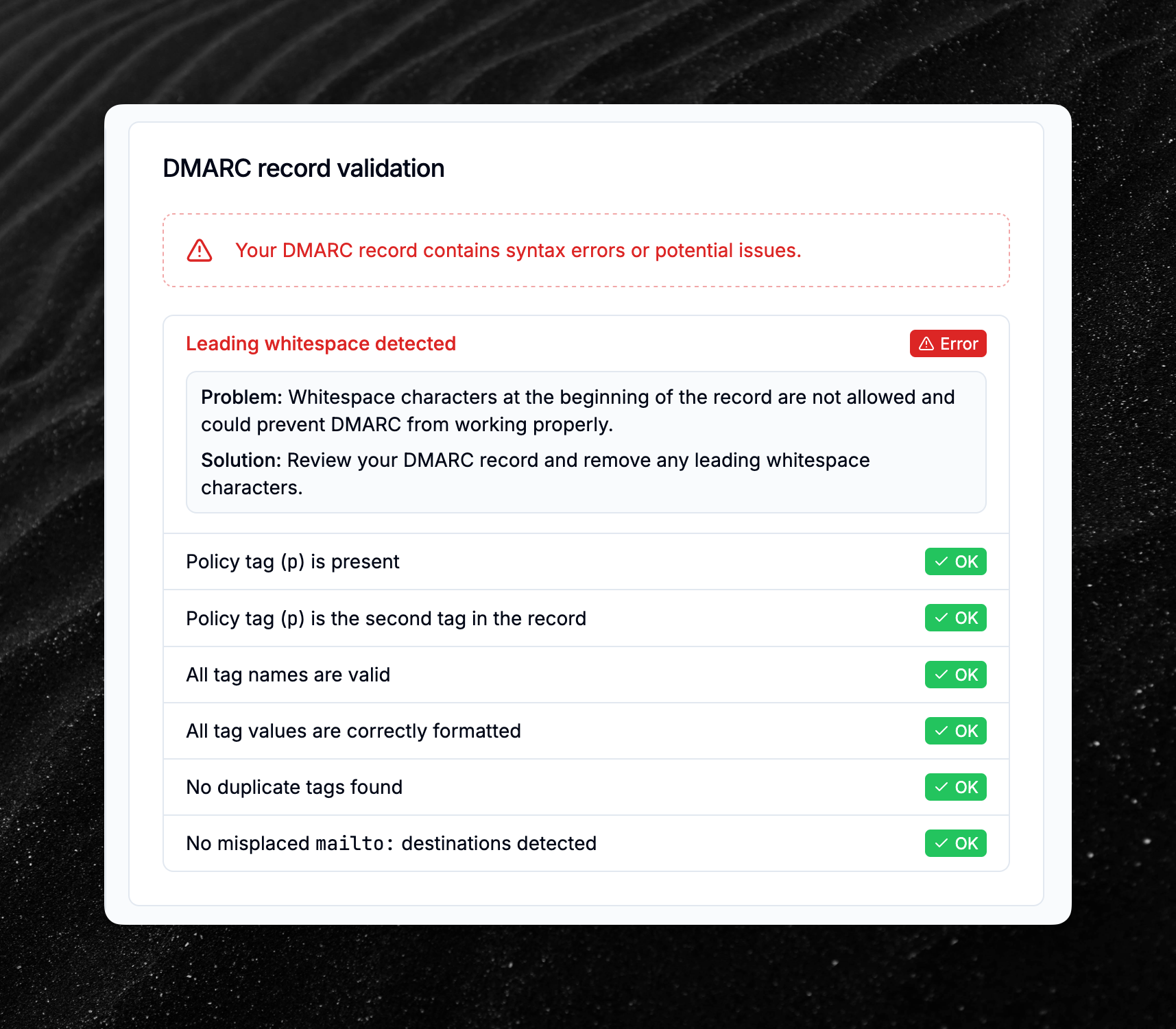
Your domains’ DMARC records are now analyzed to identify syntax issues that could prevent parsers from using DMARC correctly.
When a syntax error or potential issue is detected, you’ll find the details in the DMARC overview page. A check warning or error will also be triggered.
We currently validate the record to make sure that:
No leading whitespace is present.
Policy tag (
p) is present.Policy tag (
p) is the second tag in the record.All tag names are valid.
All tag values are correctly formatted.
No duplicate tags are present.
No misplaced
mailto:destinations are detected.
We currently don’t detect the following issues:
- Strict
fovalue compliance. - Missing
rufwhenfois present. ruaandrufURIs correctness.- A record not starting with
v=DMARC1(leading whitespace is ignored) will be discarded and not shown at all.
The validation will be improved in future updates.
Learn more in the documentation.
Default tag values are now shown in DMARC record tables
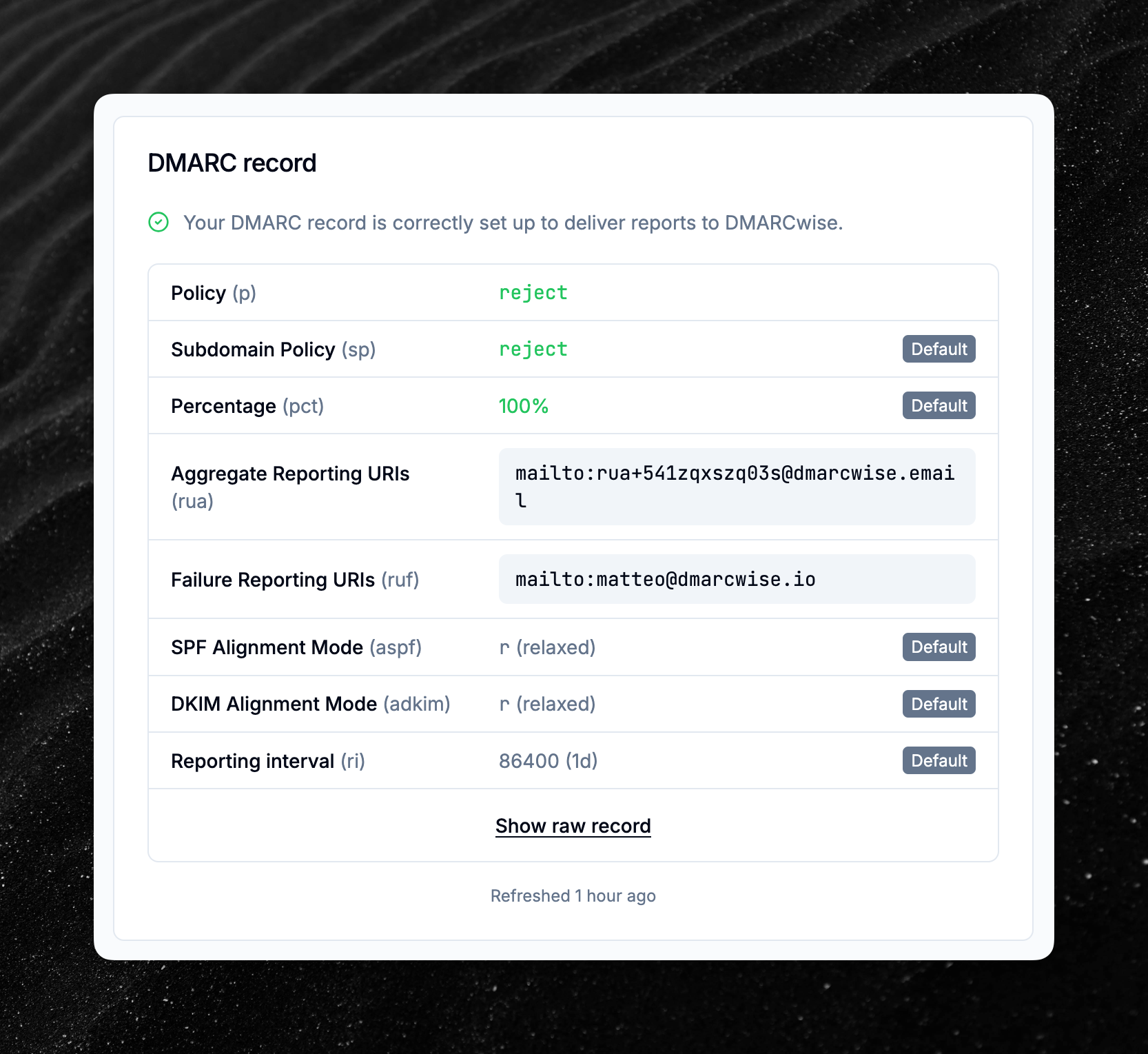
The DMARC record summary table now shows default values when a tag is not set.
For example, if you don’t specify the sp tag (subdomain policy) in your DMARC record, the UI will show that the value of p is being used as per RFC 7489.
Improved domains grouping
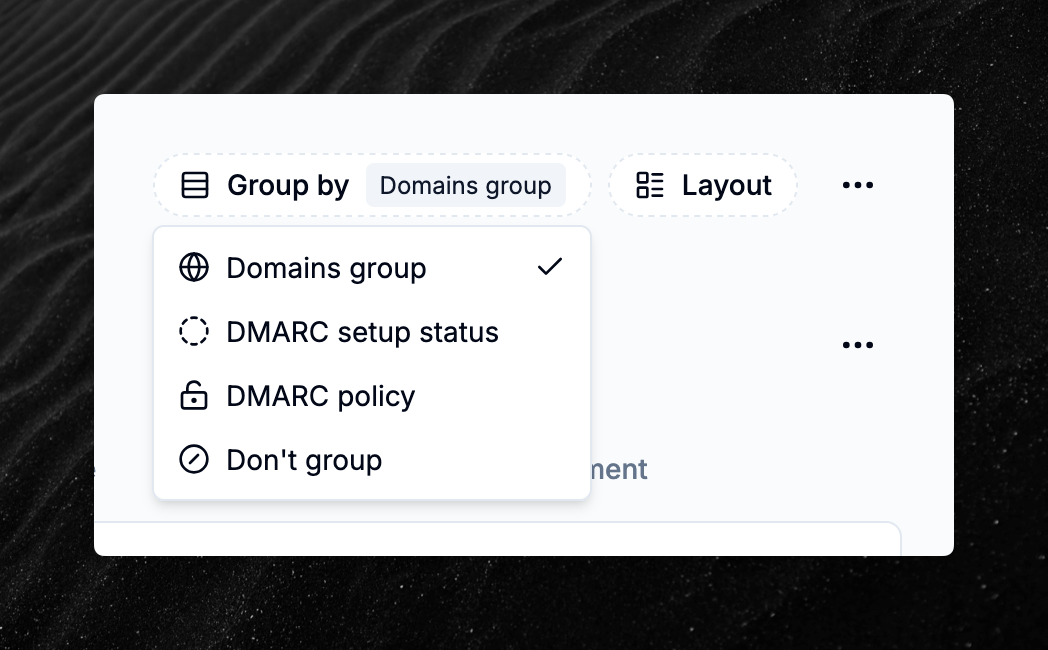
You can now group domains by domain group, DMARC setup status or DMARC policy, making it easier to identify which domains require action.
Domains import and export are now available
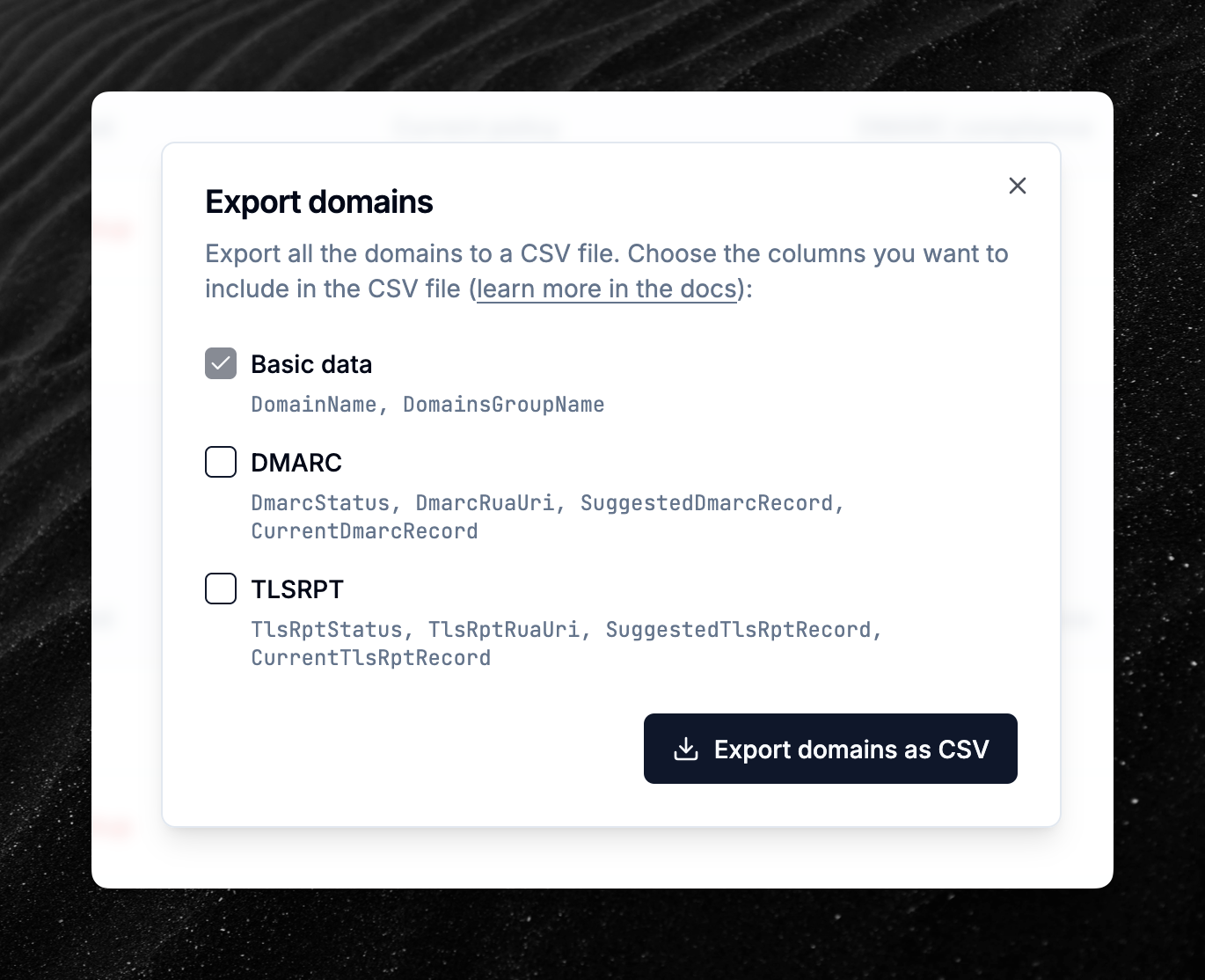
You can now bulk import and export domains from/to a CSV file to ease the management of a large number of domains.
Learn more in the documentation about importing domains and exporting domains.
Improved design of the UI for several tables and pages
We’ve just improved the design of several tables and pages in the web app.
Take a look at the before and after in the video above.
Visit the changelog archive for earlier changes.
