DMARCwise makes it simple to understand whether your email flows are correctly authenticated.
The main page to keep an eye on is the Sources page, which lists all sending sources detected in the DMARC reports:
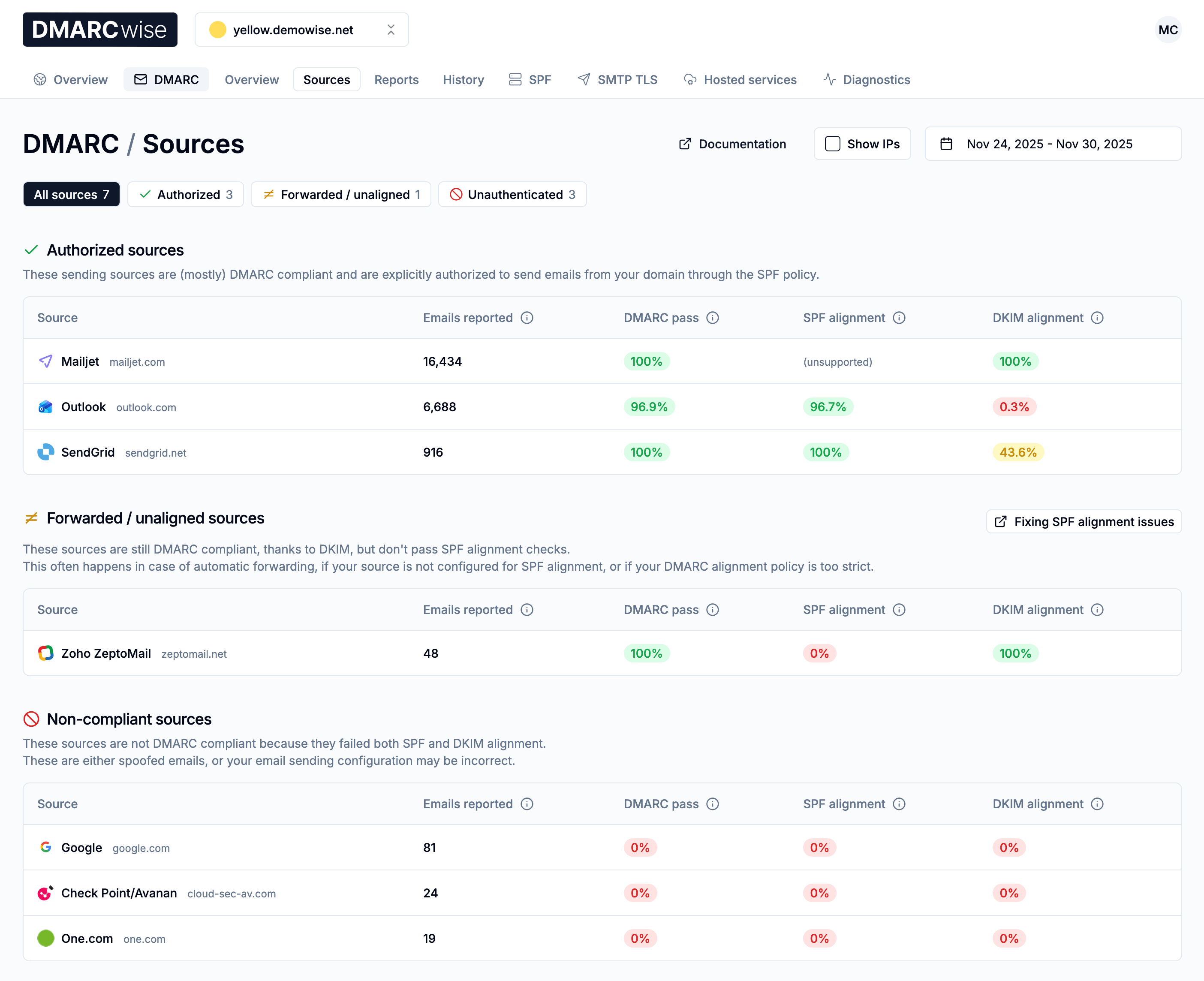
The number of sources greatly depends on how much email messages you send: it could be a few, but we’ve also seen thousands.
By default, everything in this page refers to the last week of activity by default. You can change the date interval through the date picker in the top right corner.
Read our Guide to DMARC compliance to learn more on how to use this data to achieve DMARC compliance.
Source names identification
In most cases, you should see the email service provider name as the source name (e.g. Outlook or SendGrid). We maintain our own mapping and we constantly improve it.
Sometimes a name is not available and you’ll then see just the domain under which the sending mail server is configured.
Source categories
DMARCwise groups sending sources in three categories:
- Authorized sources
- Forwarded/unaligned sources
- Non-compliant sources
Note that this categorization is best-effort and isn’t always very accurate. For example, DMARC reports don’t provide a reliable way to distinguish forwarded mail flows, so we try to deduce when this happens.
Here’s what the categories mean.
Authorized sources
Authorized sources are at least partially DMARC compliant and are explicitly authorized to send emails from your domain, primarily based on SPF.
In detail, this group contains:
- Sources that are fully aligned, on both SPF and DKIM. It’s normal if the percentage isn’t 100%, there’s always a small part of forwarded emails or temporary authentication errors that lower the compliance percentage.
- Sources that are fully SPF aligned but don’t pass DKIM or DKIM alignment. If you find yourself in this situation, check that your emails are sent with a valid and aligned DKIM signature.
- Some sources in this section may have a low SPF alignment percentage. This may be caused by your DMARC policy being too strict (look at
aspf), or by a misconfiguration of the Envelope From. Learn more in Fixing SPF alignment issues. - We also have some rules to move to this section some sources that are known to not support SPF alignment or only partially behind paid add-ons that aren’t well documented. These sources are clearly marked in the dashboard. Some prominent examples are Mailchimp and Brevo.
Forwarded/unaligned sources
Forwarded/unaligned sources usually emerge from mail servers that forwarded your emails.
Since detection of forwarding cannot be done reliably, you may also find sources that are legitimate but not SPF aligned in this section.
In more detail:
- You may identify forwarded sources by their low volume of emails, and by the fact that they are fully or mostly DKIM aligned. In fact, DKIM signatures usually survive forwarding, while SPF doesn’t.
- Some sources might not be configured for SPF alignment (often called “custom Return-Path” by email service providers). You may find these sources in this section. To fix this issue, you should check if your provider is capable of SPF alignment.
- Find more tips on SPF alignment issues in Fixing SPF alignment issues.
Non-compliant sources
Non-compliant sources failed to pass both SPF alignment and DKIM alignment, and therefore also DMARC alignment.
- If you recognize sources that belong to your organization in this section, you should identify the authentication issues as soon as possible and fix them. Running a diagnosis might help identify the issues.
- Sources that you don’t recognize in this section are likely spoofed email or forwarded emails that failed alignment. If these emails are more than a few, it means it’s especially helpful in your case to have a strict DMARC policy.
Viewing per-IP address data
In the sources page, you have the option to click the Show IPs checkbox, which will show, for each source, the IP addresses from which the reported emails were sent. This can be useful to identify one misbehaving mail server.
Source details
Clicking on a row in the sources tables will lead to a more detailed view where you’ll be able to see why SPF, SPF alignment, DKIM or DKIM alignment failed for that source, along with the specific domain names associated to SPF and the DKIM signatures.
In the DMARC source page, each row of each table has the following attributes in common:
- The From domain.
- The DMARC alignment result (pass or fail).
- The SPF authentication results and the DKIM signatures/authentication results.
Clicking on a row lets you expand it further to get an even higher level of detail. For example, in the following screenshot it’s easy to see that this email flow has a DKIM signature that is unaligned with the From domain:
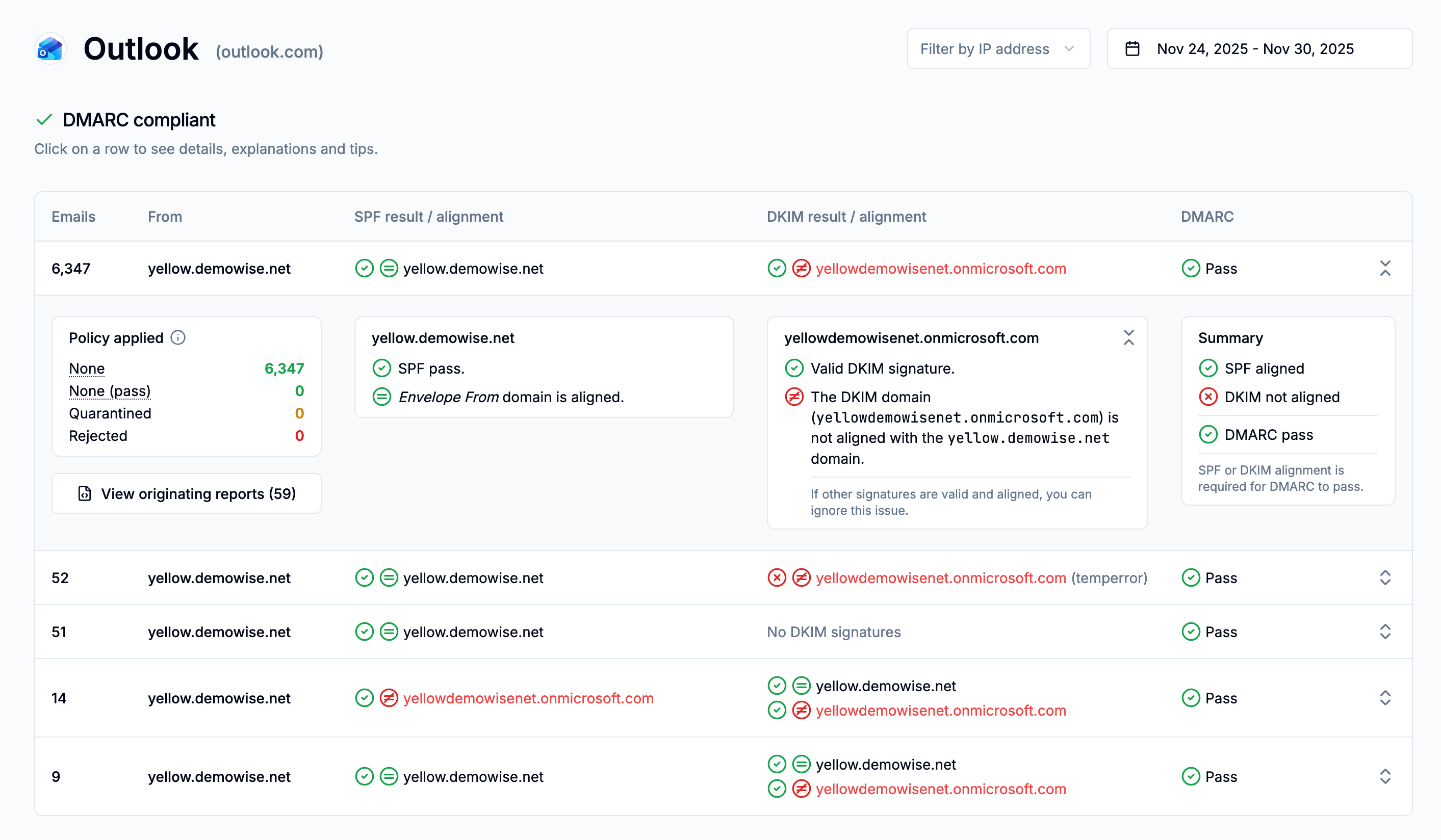
From this view you can also quickly find out which DMARC reports (and thus mail receivers) produced the data for this DMARC source. To see this list, click on View originating reports.
The list of originating reports can also sometimes be useful to identify false positives: DMARC reports are all but perfect and some report generators may sometimes omit parts of the data, like DKIM signatures. The list of reporters may help troubleshooting this kind of situation.
